Put a pin in it
Nina Berman on 29 Jan 2026
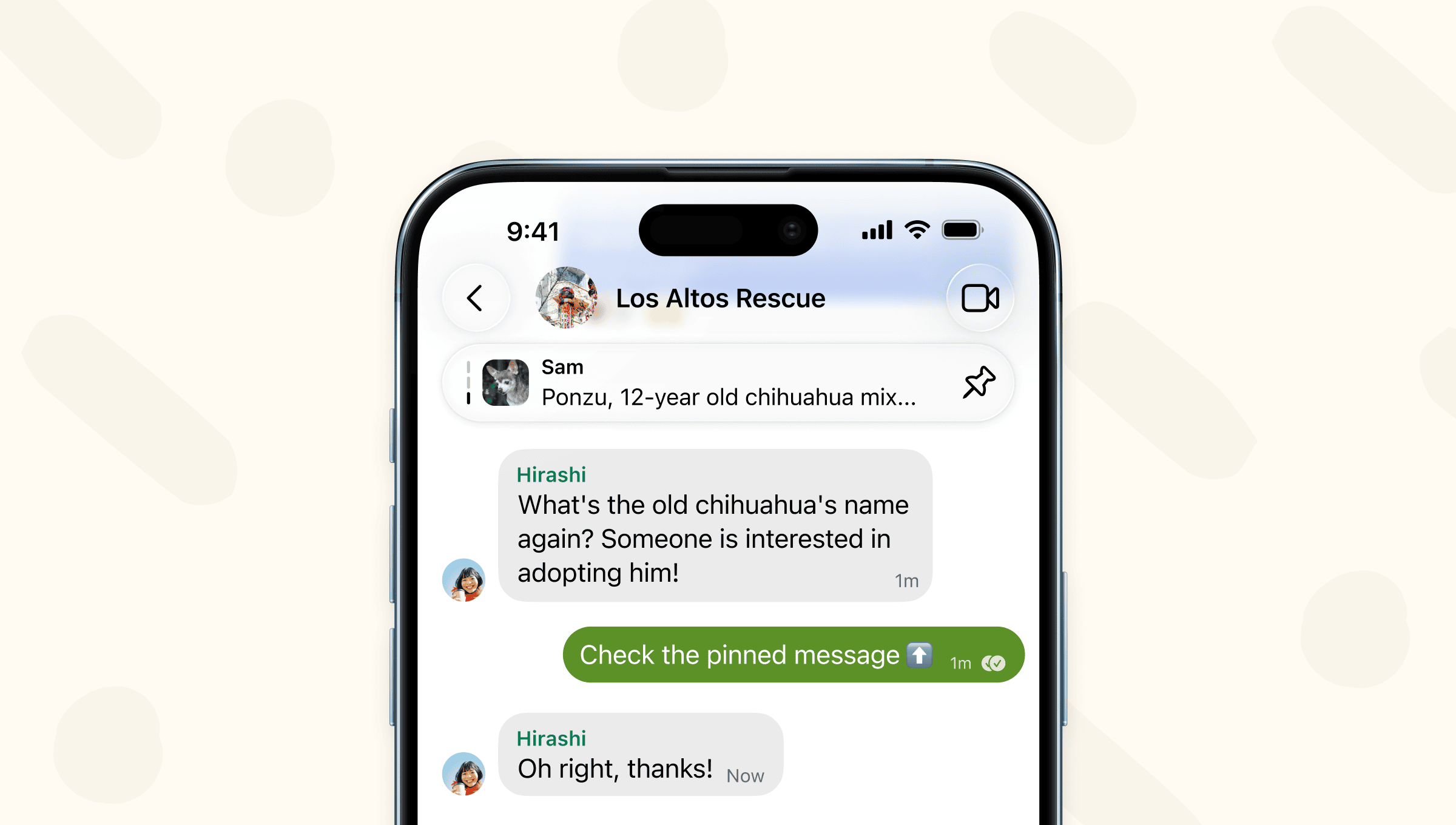
Your most frequently asked questions, dinner reservations, and vacation itineraries are already top of mind. Now they can be top of chat as well.
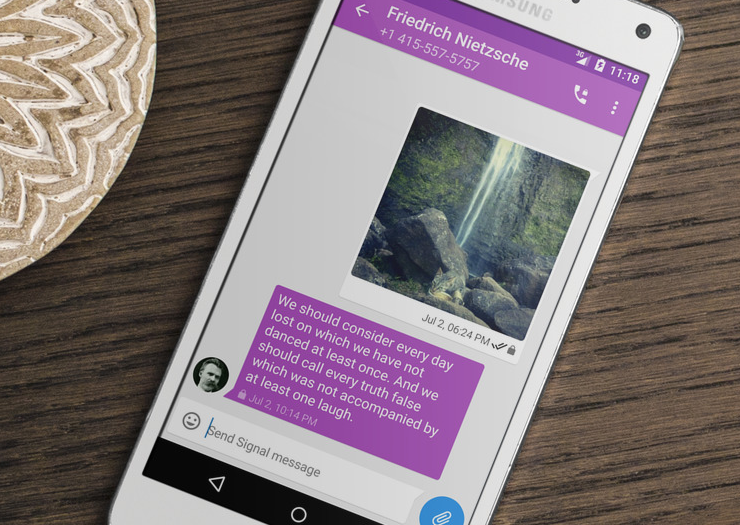
In the latest version of Signal rolling out now, you can pin your most important messages to the top of your 1-1 and group chats.
Signal Polls: Yes, no, maybe (yes!)
Nina Berman on 19 Nov 2025
Signal Protocol and Post-Quantum Ratchets
Graeme Connell and Rolfe Schmidt on 02 Oct 2025
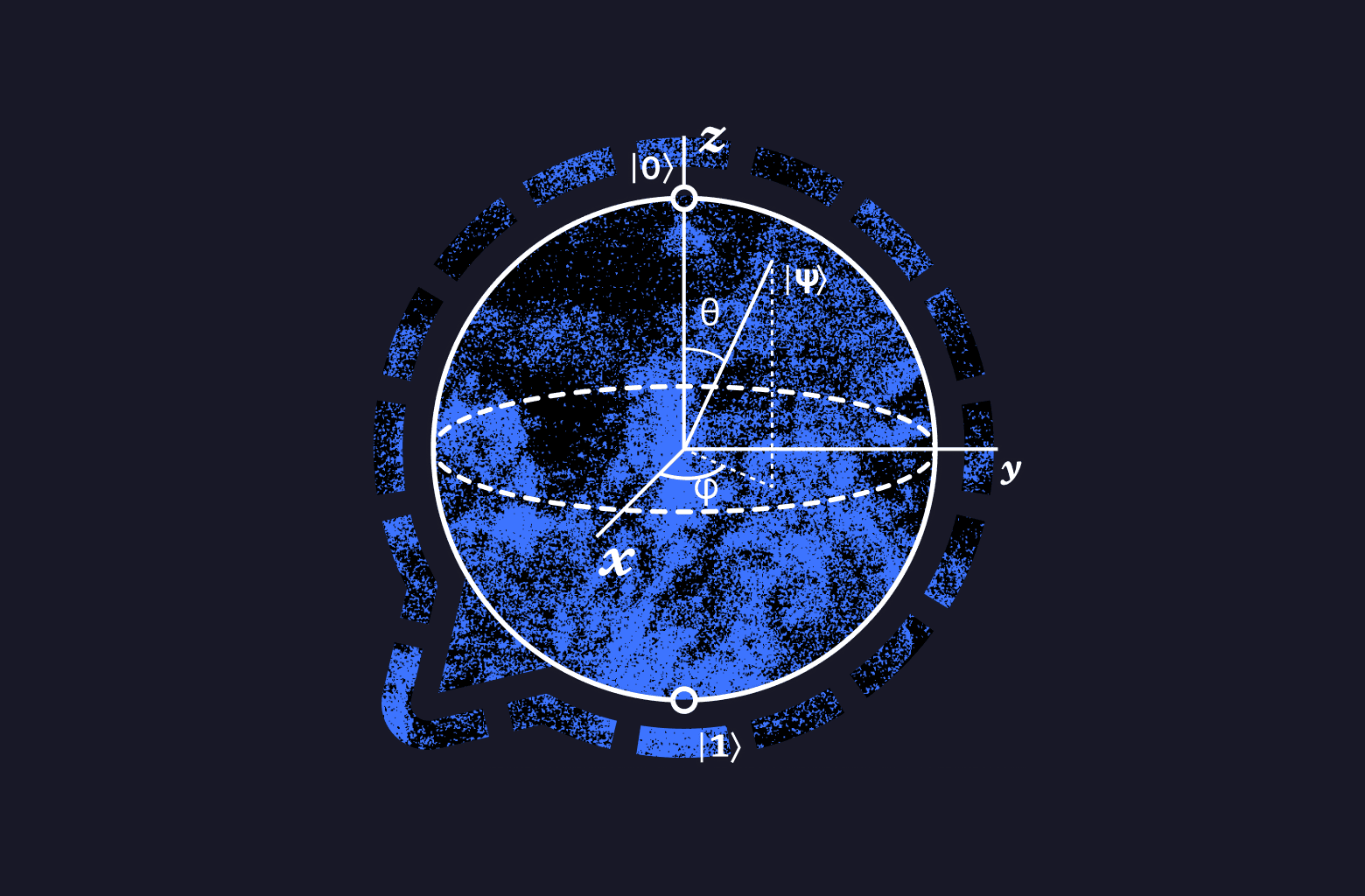
We are excited to announce a significant advancement in the security of the Signal Protocol: the introduction of the Sparse Post Quantum Ratchet (SPQR). This new ratchet enhances the Signal Protocol’s resilience against future quantum computing threats while maintaining our existing security guarantees of forward secrecy and post-compromise security.
Introducing Signal Secure Backups
jimio on 08 Sep 2025
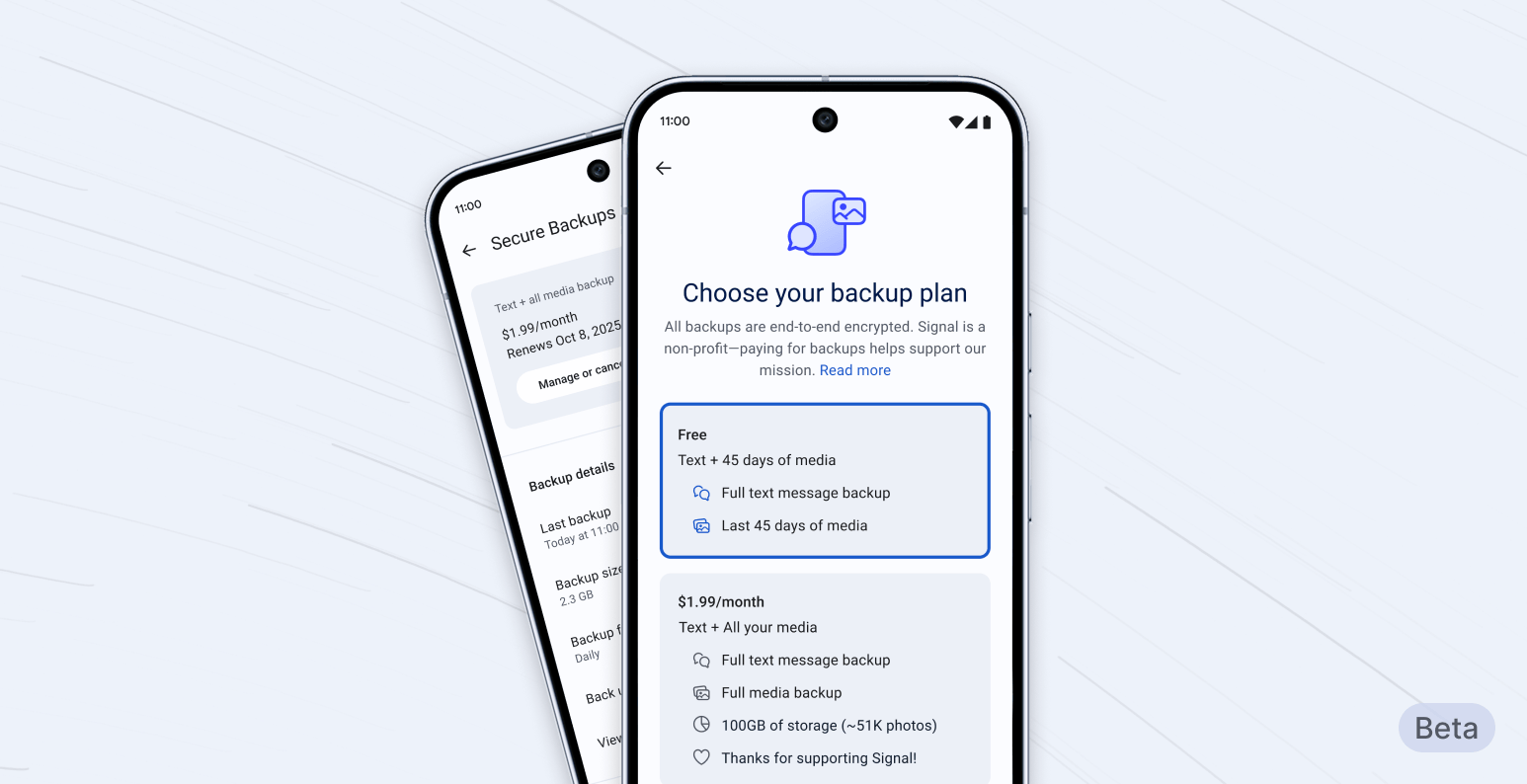
In the past, if you broke or lost your phone, your Signal message history was gone. This has been a challenge for people whose most important conversations happen on Signal. Think family photos, sweet messages, important documents, or anything else you don’t want to lose forever. This explains why the most common feature request has been backups; a way for people to get Signal messages back even if their phone is lost or damaged.
After careful design and development, we are now starting to roll out secure backups, an opt-in feature. This first phase is available in the latest beta release for Android. This will let us further test this feature in a limited setting, before it rolls out to iOS and Desktop in the near future.
By Default, Signal Doesn't Recall
jlund on 21 May 2025
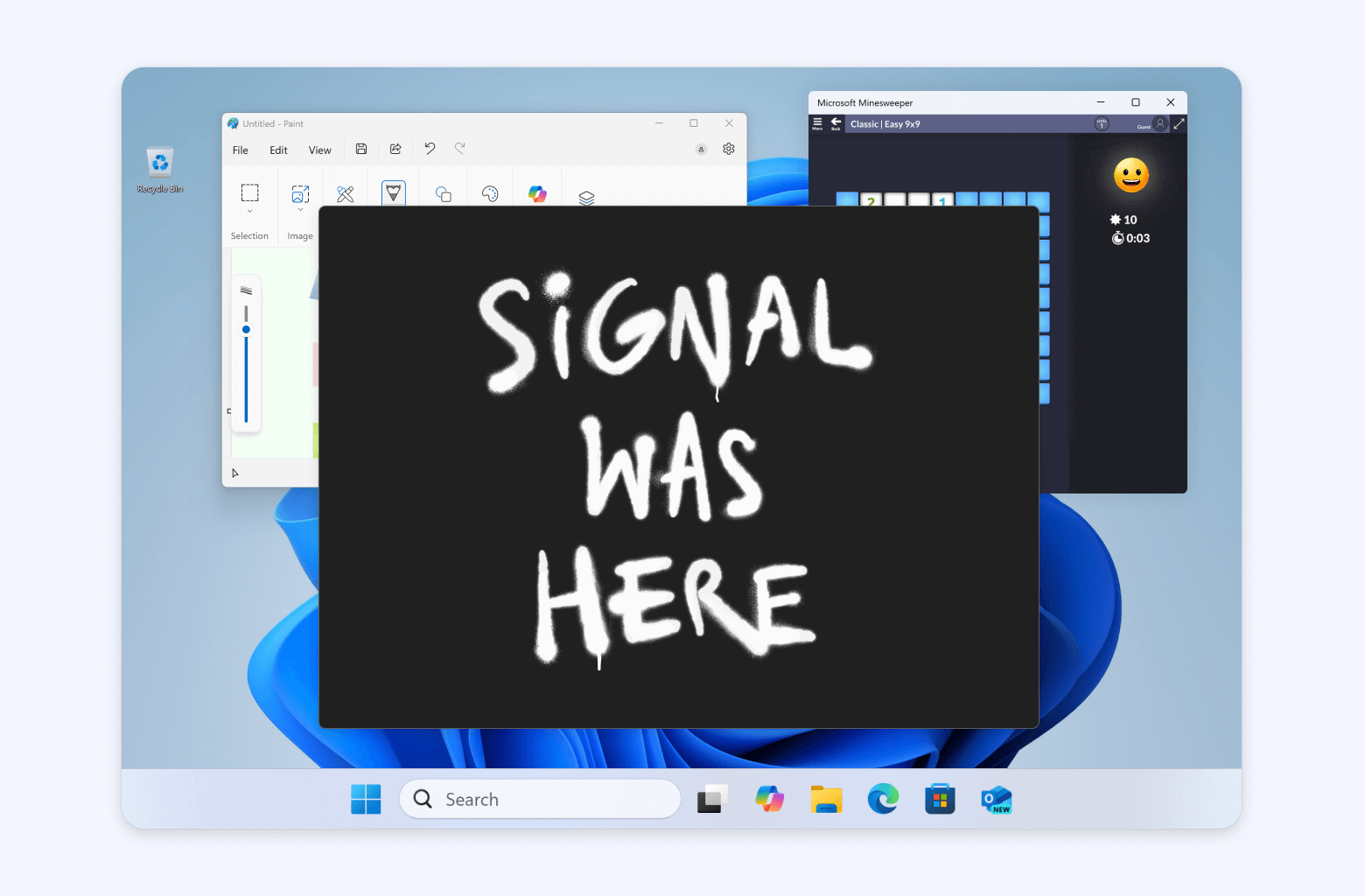
Signal Desktop now includes support for a new “Screen security” setting that is designed to help prevent your own computer from capturing screenshots of your Signal chats on Windows. This setting is automatically enabled by default in Signal Desktop on Windows 11.
If you’re wondering why we’re only implementing this on Windows right now, it’s because the purpose of this setting is to protect your Signal messages from Microsoft Recall.
A Synchronized Start for Linked Devices
ravi-signal on 27 Jan 2025
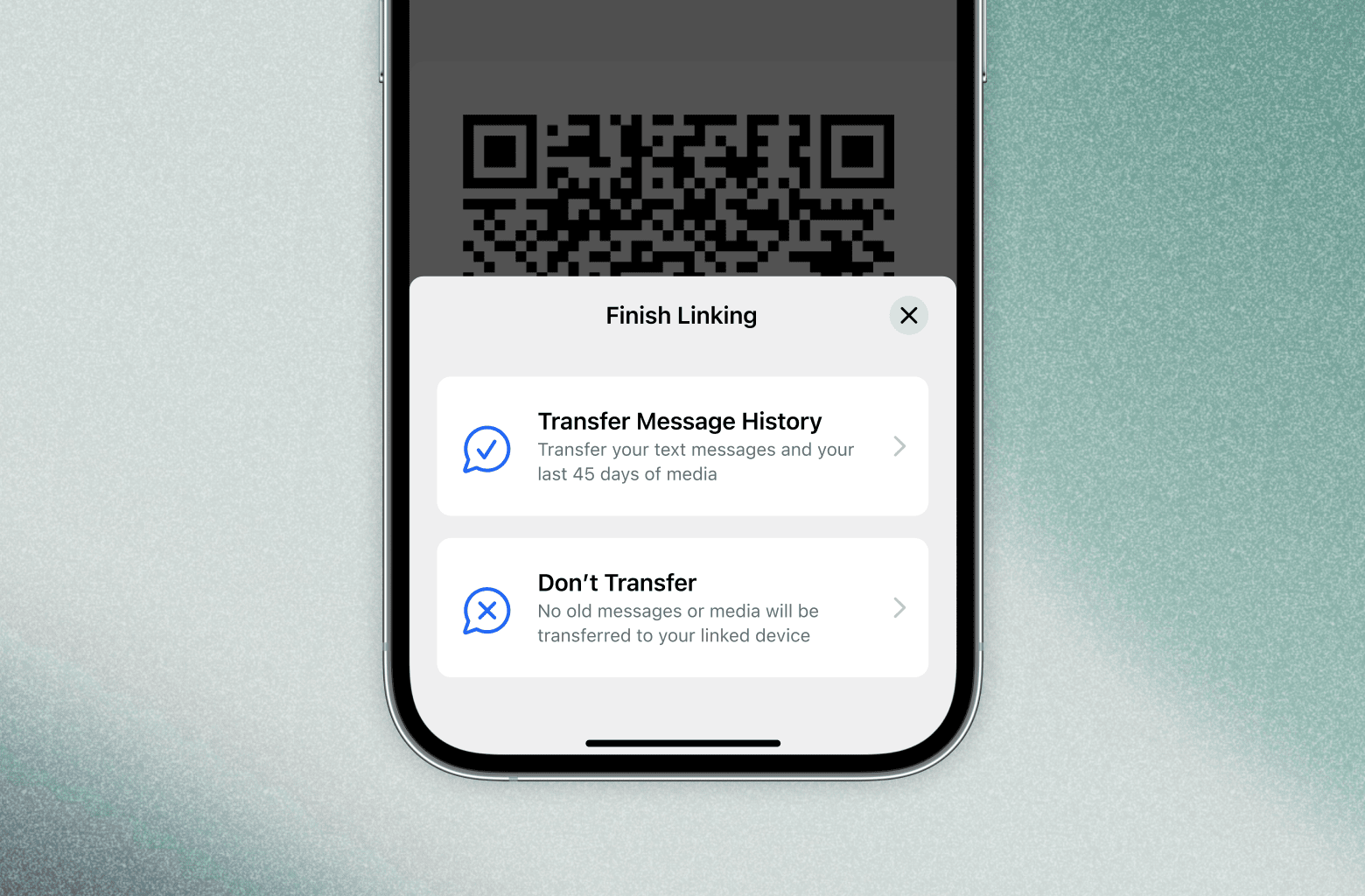
With Signal on Desktop and iPad, you can link your primary Android or iOS account with another device, letting you check and respond to messages in both places or conduct video meetings and calls from the comfort of a bigger screen.
Signal’s upcoming beta releases will also introduce the option to transfer your messages and media when you link your primary Signal device to a new Desktop or iPad. Instead of starting fresh, and having only new messages show up, you can choose to bring your chats and your last 45 days of media with you. Or, you can choose not to.
Improving Private Signal Calls: Call Links & More
Nina Berman on 11 Nov 2024
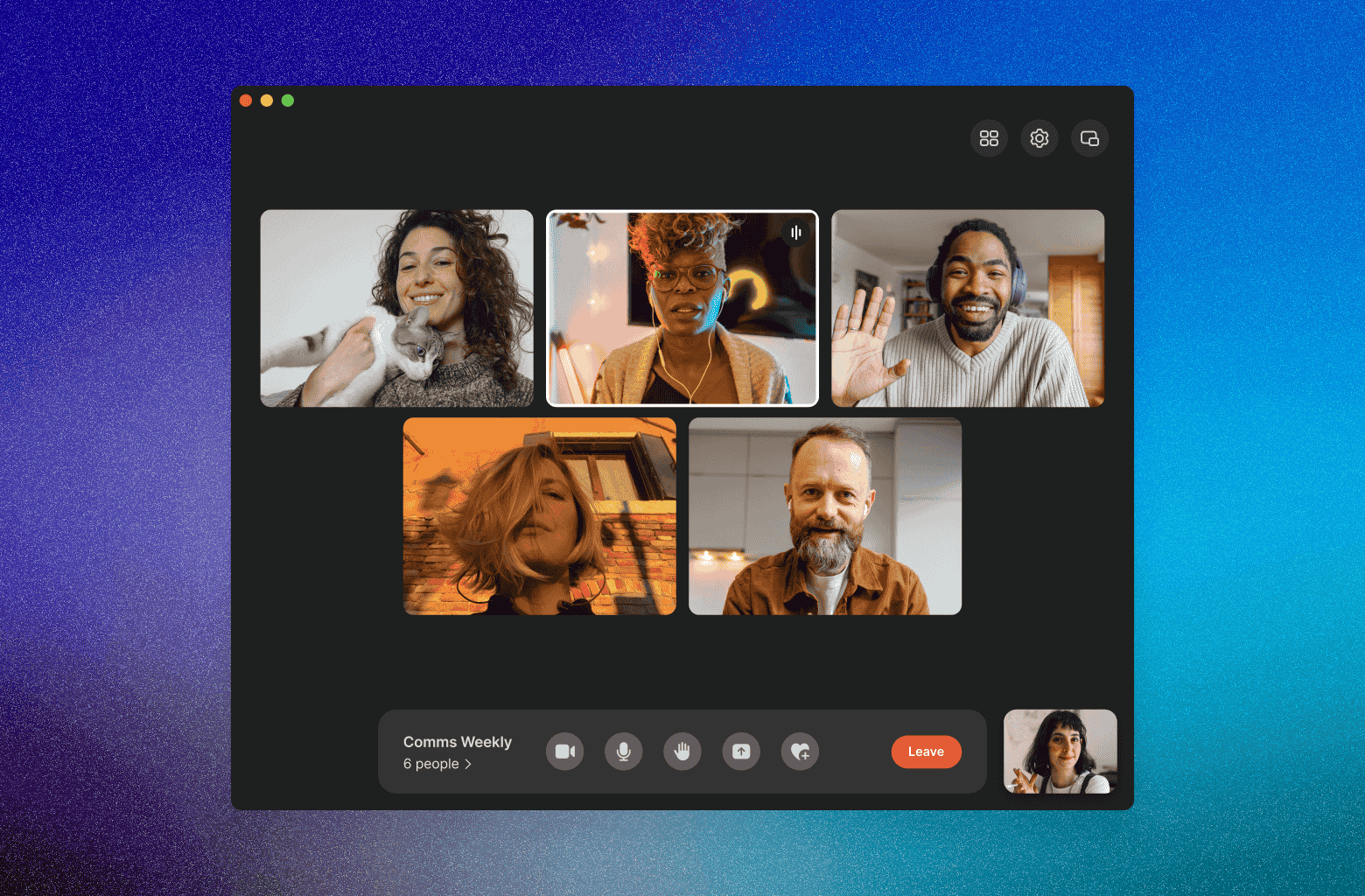
If you love group calls on Signal, but don’t want to create a group chat for every combination of your friends or colleagues, you’re in luck. Today we’re launching call links: Share a link with anyone on Signal and in just a tap or click they can join the call. No group chat required.
Proxy Please: Help People Connect to Signal
Meredith Whittaker on 09 Aug 2024
Several countries have recently blocked Signal, leaving their residents without a trusted and safe place to communicate.
To help in this situation, Signal provides a built-in censorship circumvention feature and also includes support for a simple TLS proxy that can bypass these blocks in many circumstances and let people communicate privately.
Keep your phone number private with Signal usernames
Signal on 20 Feb 2024
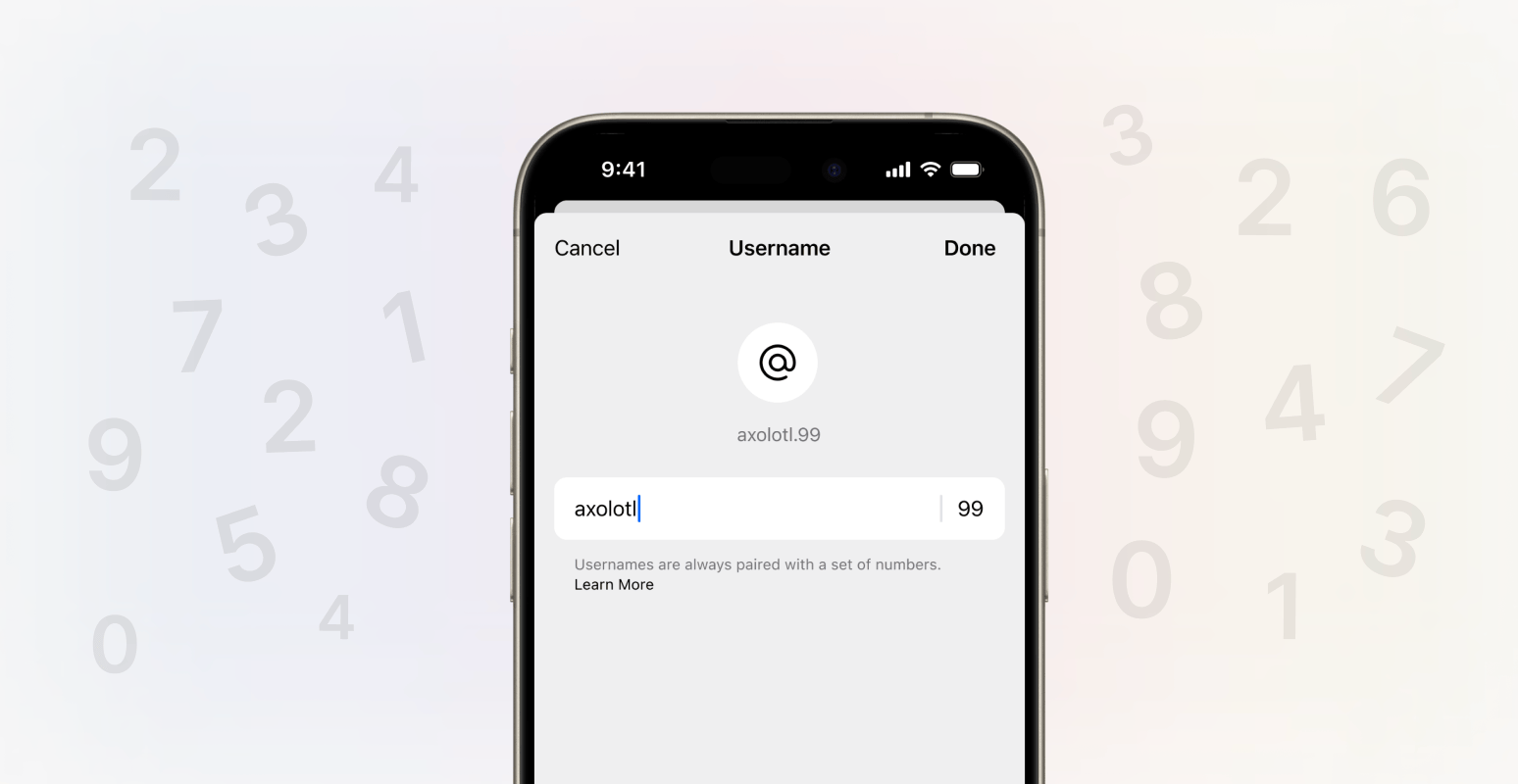
Signal’s mission and sole focus is private communication. For years, Signal has kept your messages private, your profile information (like your name and profile photo) private, your contacts private, and your groups private – among much else. Now we’re taking that one step further, by making your phone number on Signal more private.
Here’s how:
Trend report: Use Signal
nina-signal on 13 Dec 2023
New long-sleeve shirts and tote bags fresh from the Signal test kitchen:
We build Signal for people all over the world. So, of course we wanted to reflect that same global outlook in our merch.
Privacy is Priceless, but Signal is Expensive
Meredith Whittaker and Joshua Lund on 16 Nov 2023

Signal is the world’s most widely used truly private messaging app, and our cryptographic technologies provide extra layers of privacy beyond the Signal app itself. Since launching in 2013, the Signal Protocol—our end-to-end encryption technology—has become the de facto standard for private communication, protecting the contents of billions of conversations in WhatsApp, Google Messages, and many others. Signal also continues to invest in research and development in the pursuit of extending communications privacy. This commitment underlies our recent work to add a layer of quantum resistance to the Signal Protocol, and our previous work on metadata protection technologies that help keep personal details like your contact list, group membership, profile name, and other intimate information secure. This singular focus on preserving the ability to communicate privately is one reason that we work in the open, documenting our thinking and making our code open source and open to scrutiny—so you don’t have to take our word for it.
New Features Roll Call: Fall 2023
nina-signal on 08 Nov 2023

You should be able to communicate without worrying that every gossip tidbit, meme, or joke you share and who you share it with will get churned up into fodder for targeted ads or used to train an AI model. You also shouldn’t have to strip your communications down to the barest and most utilitarian version of relaying information.
This is why Signal is dedicated to providing a truly private messaging app, and why we work to constantly make the experience better for everyone who uses it.
We want you to know about the improvements we’re making in Signal, even the smaller ones that simply make the app nicer to use. So, starting here we’re publishing a periodic New Features Roll Call, reviewing multiple new features and quality of life improvements in one place.
Quantum Resistance and the Signal Protocol
ehrenkret on 19 Sep 2023
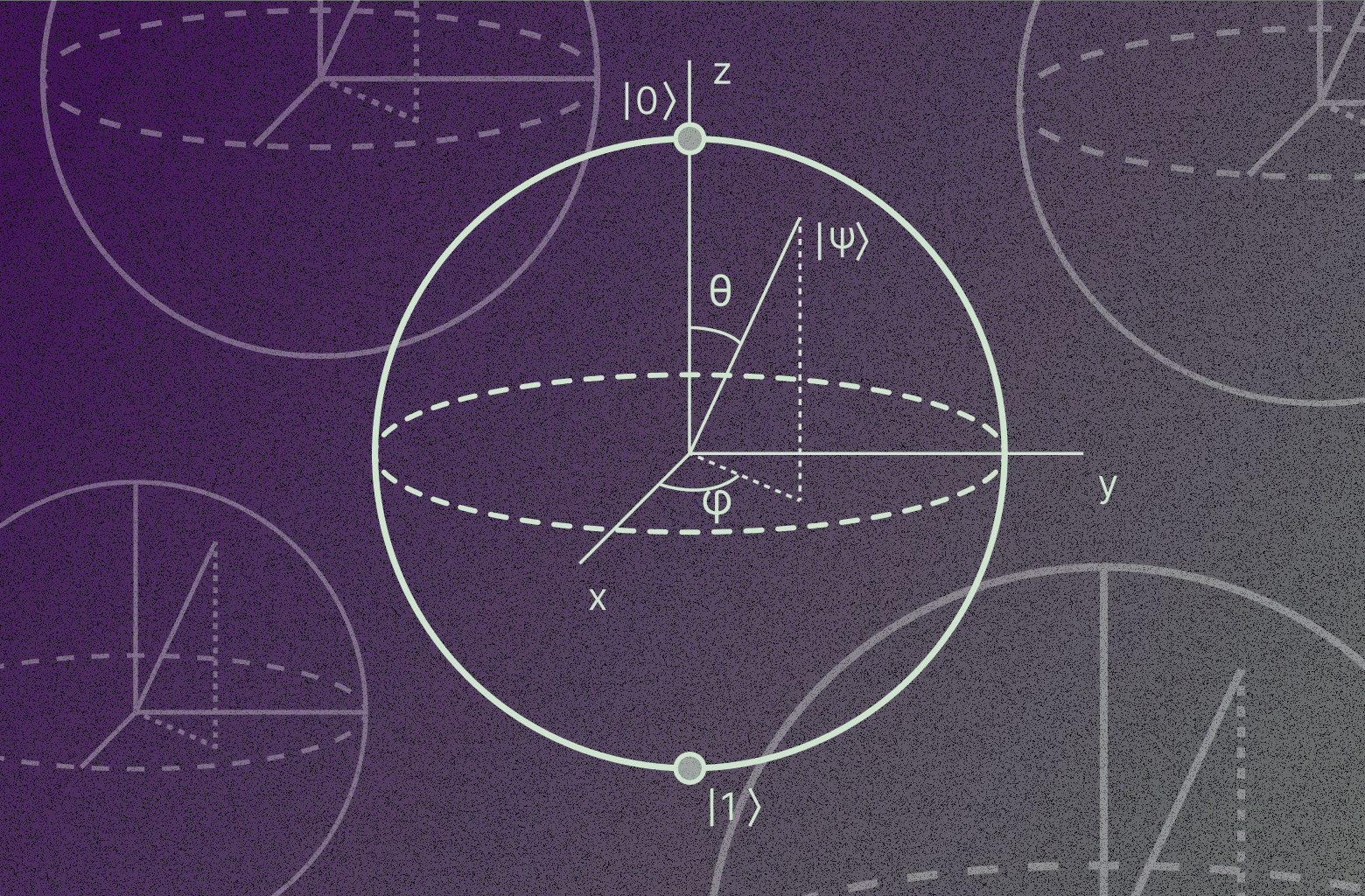
The Signal Protocol is a set of cryptographic specifications that provides end-to-end encryption for private communications exchanged daily by billions of people around the world. After its publication in 2013, the Signal Protocol was adopted not only by Signal but well beyond. Technical information on the Signal Protocol can be found in the specifications section of our docs site.
Today we are happy to announce the first step in advancing quantum resistance for the Signal Protocol: an upgrade to the X3DH specification which we are calling PQXDH. With this upgrade, we are adding a layer of protection against the threat of a quantum computer being built in the future that is powerful enough to break current encryption standards.
This post is written to introduce this work to non-experts, and will review what quantum computing is and the challenges it presents for current cryptographic algorithms, before providing a high level overview of how we are adapting our specifications to answer these challenges. If you would like to skip this summary and explore our PQXDH specification in depth, you can read our technical whitepaper here.
Signal exists to provide people everywhere with a tool for real private communication. That’s our only goal, and we take it very seriously. We’re structured as a nonprofit to ensure that market forces can never put profit or expediency over the safety of those who rely on us. Our work also resonates beyond the Signal app. The Signal Protocol has become the foundation for end-to-end encryption technology that is used and trusted by many private messaging services to protect billions of messages every day.
We recognize that privacy is a human right and that free expression and the ability to dissent are fundamental to a safe and vibrant society. But the current state of the Online Safety Bill in the UK puts the future of privacy and expression in grave jeopardy.
Signal is for everyone, and everyone is different
nina-signal on 07 Mar 2023
The tech industry–its products, conceptual frameworks, linguistic conventions, and cultural norms–is largely centered in the US (and, increasingly, China. But we’re focused here on the US, where Signal is based). This is not because the US has better programmers or more visionary entrepreneurs, but due primarily to historical material conditions. For example, early investments in networked computation from the US military, which happened around the same time that the US was becoming a global superpower, which was followed by the privatization and then commercialization of networked computation, then the dot com boom, etc. etc., and here we are.
Story Time
nina-signal on 07 Nov 2022
If your favorite way to update your friends about life disappears in 24 hours, we’ve got some happy news for you.
Stories are now available on Signal for Android and iOS, with Desktop coming soon!
Removing SMS support from Signal Android (soon)
nina-signal on 12 Oct 2022
For many years, the Signal app on Android has supported sending and receiving plaintext SMS and MMS messages in addition to Signal messages. SMS and MMS are standardized communication protocols that allow mobile devices to send and transmit messages, and most people picking up their phone to text or share memes don’t really think about them.
To give some context, when we started supporting SMS, Signal didn’t exist yet. Our Android app was called TextSecure and the Signal encryption protocol was called Axolotl. Almost a decade has passed since then, and a lot has changed.
Signal is currently blocked in Iran. To help people in the country access Signal, we are republishing and revising a post that we originally posted in February, 2021 during a very similar situation in Iran.
If you are willing and able, please follow the instructions below to set up a proxy server that will enable people in Iran to connect to Signal. We are grateful to the community who pitches in to help each other during these moments.
If you are currently running a proxy, you will need to make some updates to ensure it continues to function. Update instructions are here.
A Message from Signal's New President
meredith-signal on 06 Sep 2022
On September 12 I’ll be stepping into the role of Signal’s President, a new position created in collaboration with Signal’s leadership. I am thrilled, and I can’t think of a more meaningful use of my time, or a greater honor. I’ve been a friend, admirer, and champion of Signal since it was RedPhone and TextSecure, and in 2020 I joined Signal’s Board of Directors, helping inform high-level strategy and direction. So in many ways this is a happy step on a long continuum, not a dramatic change.
Signal is more important now than ever, and I expect this to stay true well into the future. As President I will dedicate myself to helping Signal build a long taproot so it can grow and thrive in dynamic climates. In this role I will be working with Signal’s CEO and leadership, with a particular focus on guiding Signal’s strategy, ensuring our financial sustainability, sharpening and broadening Signal’s public communications, and whatever else is needed to strengthen the app and the org.
Private doesn’t mean lonely. Signal’s mission is to help you connect with people in a secure way. This means that you need to know which of your contacts are also on Signal. This is called “contact discovery” and it’s an essential part of any messaging app.
Most other communications apps enable contact discovery by maintaining their own internal social graph or by uploading and storing your full address book on their servers. But Signal enables you to find and connect with people in a privacy-preserving way. In short, we let you see which of your friends use Signal, but we don’t want to know who your friends are. Letting you know which of your contacts are using Signal while preserving the privacy of your social map requires some complex engineering choices on our end.
In this post, we’ll be diving into some new ways that improve our ability to handle contacts in a private way. That’s right folks. We’re getting technical. We’re talking enclaves and memory access patterns. [If you’ve never heard of an enclave before, don’t worry. We’ll explain it soon.]
Our new method is faster and more efficient. It lays the groundwork for the introduction of usernames and phone number privacy which will offer new privacy controls around your phone number’s visibility on Signal.
Signal Your Support
aruna100 on 16 May 2022
People around the world count on Signal for things as simple as sharing moments of celebration like a graduation or as high stakes as coordinating a protest. We’ve got your back no matter what! As we’ve seen in recent times from moments of civil unrest to demonstrations for democracy, people turn to Signal for private and even lifesaving communications.
Day in and day out, the team at Signal is working to keep your chats, voice, and video calls safe and private. It’s our mission. It’s also the reason why, unlike most other tech companies, we are structured as a nonprofit. We aren’t driven by profit and don’t make our money from your data or from advertising revenue. As a nonprofit, our whole focus is building safe, secure communication tools for you.
You Can Change Your Number
jimio on 07 Feb 2022
Millions of people worldwide rely on Signal every day for secure and private communication. Some of these people change their phone number, but want to continue using Signal without registering for a new account. We now provide the ability to change the phone number on your Signal account, while retaining all of your chats, profile information, and groups.
New year, new CEO
moxie0 on 10 Jan 2022
It’s a new year, and I’ve decided it’s a good time to replace myself as the CEO of Signal.
I have now been working on Signal for almost a decade. It has always been my goal for Signal to grow and sustain beyond my involvement, but four years ago that would still not have been possible. I was writing all the Android code, was writing all of the server code, was the only person on call for the service, was facilitating all product development, and was managing everyone. I couldn’t ever leave cell service, had to take my laptop with me everywhere in case of emergencies, and occasionally found myself sitting alone on the sidewalk in the rain late at night trying to diagnose a service degradation.
Signal released end-to-end encrypted group calls a year ago, and since then we’ve scaled from support for 5 participants all the way to 40. There is no off the shelf software that would allow us to support calls of that size while ensuring that all communication is end-to-end encrypted, so we built our own open source Signal Calling Service to do the job. This post will describe how it works in more detail.
Become a Signal Sustainer
moxie0 on 01 Dec 2021
Signal has no data to sell, no advertisers to sell it to, and no shareholders to benefit from such a sale. We’re building a different kind of tech – where your data stays in your hands – but we’re also building a different kind of tech organization. One without investors, quarterly earnings calls, or share price considerations. While the model for conventional tech companies incentivizes them to build products for your data rather than for you, Signal’s nonprofit structure is designed so that the only way value can accrue is in the experience of using the app; the only place it can accrue is in the hands of the people who use it.
Improving first impressions on Signal
jimio on 01 Nov 2021
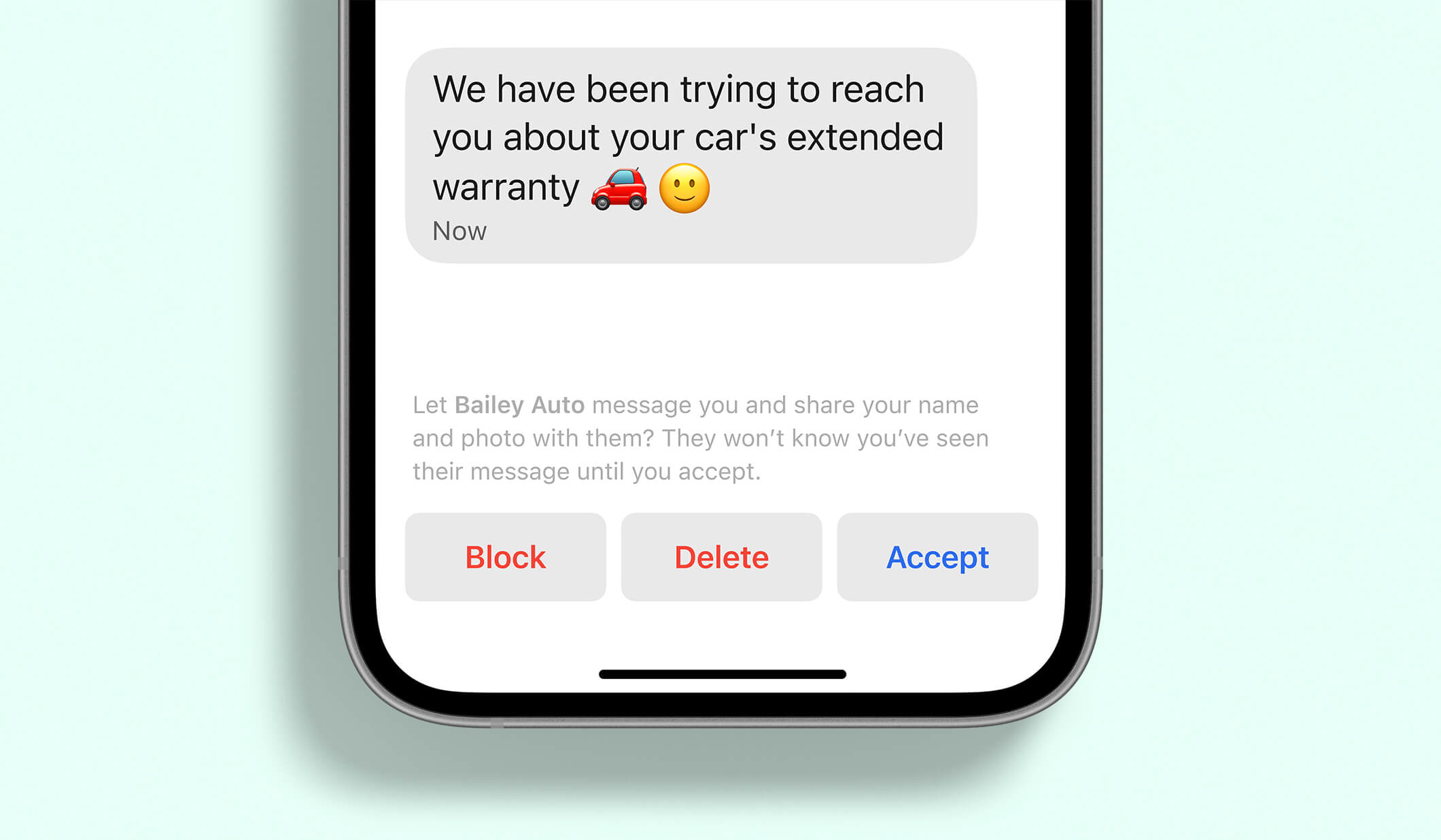
The phenomenon of unsolicited and unwanted messaging dates back to the earliest communication platforms: from prehistoric cave graffiti and postal chain letters to popup ads and robocalls. To prevent spam, most online services rely on large-scale inspection of plaintext conversation content or detailed social-graph analysis to determine who is saying what to whom and whether or not that should be allowed. At Signal, we build on a foundation of privacy and do not have access to that type of data or metadata.
We build Signal in the open, with publicly available source code for our applications and servers. To keep Signal a free global communication service without spam, we must depart from our totally-open posture and develop one piece of the server in private: a system for detecting and disrupting spam campaigns. Unlike encryption protocols, which are designed to be provably secure even if everyone knows how they work, spam detection is an ongoing chore for which there is no concrete resolution and for which transparency is a major disadvantage. If we put this code on the Internet alongside everything else, spammers would just read it and adjust their tactics to gain an advantage in the cat-and-mouse game of keeping spam off the network. The Signal protocols, cryptography, and source code are peer reviewed, shared for independent inspection, and provably private by design. We are bound by these security guarantees, so that your conversations and contacts remain as private and protected as ever, even if we keep spam-fighting tools out of sight.
Embrace ephemerality with default disappearing messages
jimio on 10 Aug 2021
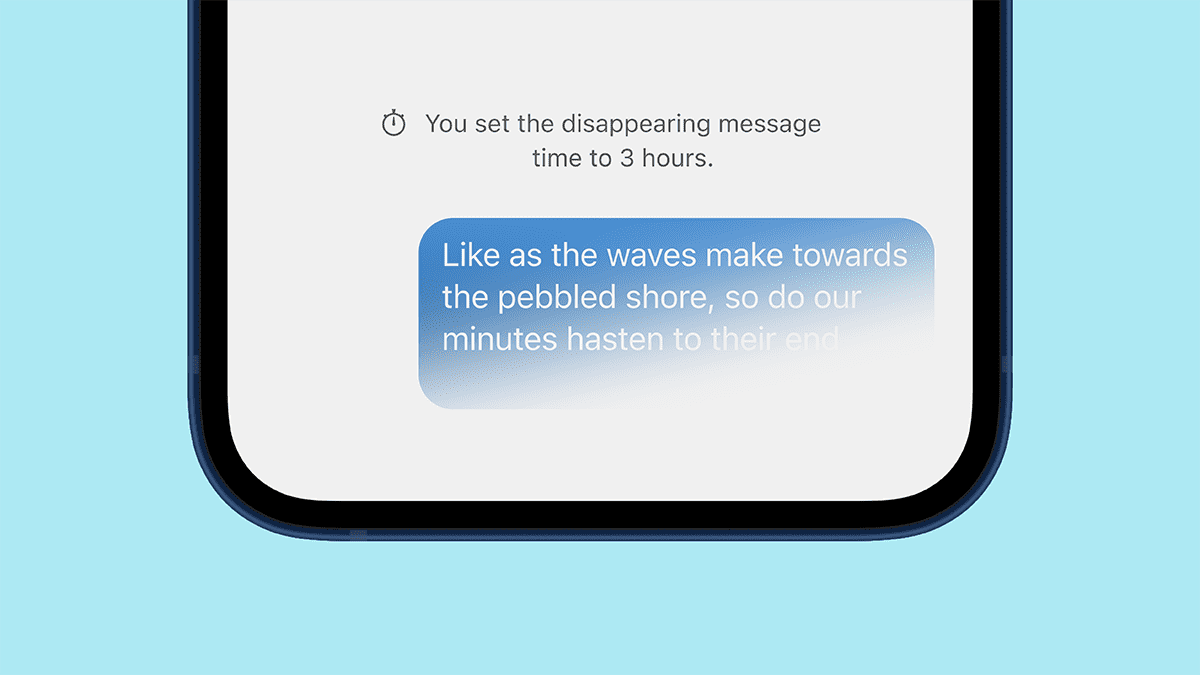
As the norms for how people connect have changed, much of the communication that once took place through the medium of coffee shops, bars, and parks now takes place through the medium of digital devices. One side effect of this shift from analog to digital is the conjoined shift from the ephemeral to the eternal: words once transiently spoken are now – more often than not – data stored forever.
We’ve designed Signal so that your data always stays in your hands. We think there’s something special about sharing a private fleeting moment between friends, so Signal also supports disappearing messages. Now, we’ve added the ability to preconfigure all conversations you initiate with a default disappearing messages timer.
The Instagram ads Facebook won't show you
junh3 on 04 May 2021
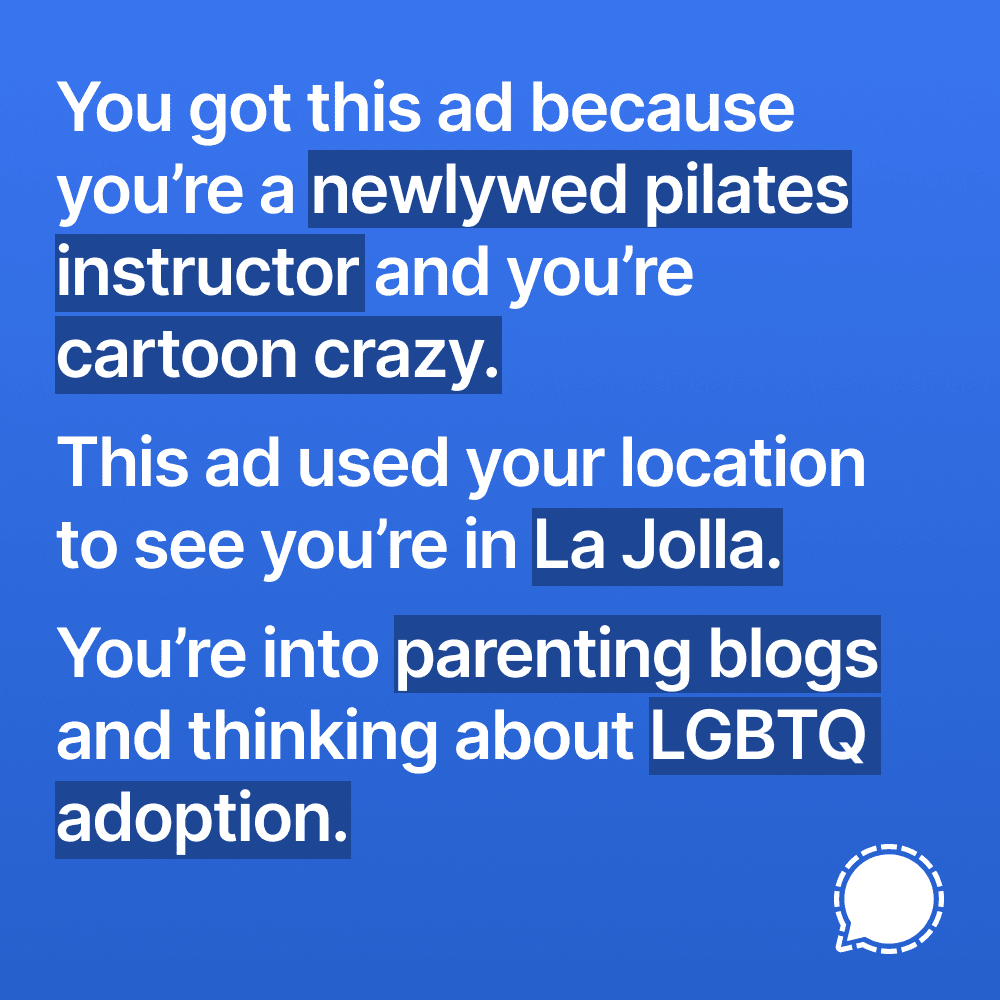
Companies like Facebook aren’t building technology for you, they’re building technology for your data. They collect everything they can from FB, Instagram, and WhatsApp in order to sell visibility into people and their lives.
This isn’t exactly a secret, but the full picture is hazy to most – dimly concealed within complex, opaquely-rendered systems and fine print designed to be scrolled past. The way most of the internet works today would be considered intolerable if translated into comprehensible real world analogs, but it endures because it is invisible.
Cellebrite makes software to automate physically extracting and indexing data from mobile devices. They exist within the grey – where enterprise branding joins together with the larcenous to be called “digital intelligence.” Their customer list has included authoritarian regimes in Belarus, Russia, Venezuela, and China; death squads in Bangladesh; military juntas in Myanmar; and those seeking to abuse and oppress in Turkey, UAE, and elsewhere. A few months ago, they announced that they added Signal support to their software.
Their products have often been linked to the persecution of imprisoned journalists and activists around the world, but less has been written about what their software actually does or how it works. Let’s take a closer look. In particular, their software is often associated with bypassing security, so let’s take some time to examine the security of their own software.
Update on beta testing payments in Signal
junh3 on 13 Apr 2021
As the world stands today, the future of transaction privacy does not look great. The existing landscape is dominated by traditional credit companies, who over the past decade have been steadily pushing their networks for increased access to user data. They (and their data customers) are on a track to getting SKU level data of every purchase everyone makes everywhere. There are other contenders, such as regional online payments networks (like Venmo in the US), but the data story there is similar.
This is not a future we are particularly excited about. At Signal, we want to help build a different kind of tech – where software is built for you rather than for your data – so these are trends that we watch warily.
Help us test payments in Signal
junh3 on 06 Apr 2021

The latest Signal betas are rolling out today. Inside, you’ll find performance enhancements, a slew of bug fixes, improvements to the mute settings, and if you’re in the United Kingdom, you’ll see support for Signal Payments – a new feature that enables you to send and receive privacy focused payments as easily as sending or receiving a message. This is a beta feature in a beta build, but for those in the United Kingdom living life on the edge, please help us test and give feedback.
Help users in Iran reconnect to Signal
jlund on 04 Feb 2021
Just over a week ago, we announced that Iranian censors had started blocking all Signal traffic in the country. As an interim solution to help people in Iran get connected again, we’ve added support in Signal for a simple TLS proxy that is easy to set up, can be used to bypass the network block, and will securely route traffic to the Signal service.
This new connection method is supported in the latest Signal Android beta release, and will be rolling out to production users in a few days. Our hope is that this will help many people in Iran start sending and receiving messages again while we continue to explore additional censorship circumvention techniques that will work there.
No, Cellebrite cannot 'break Signal encryption.'
moxie0 on 23 Dec 2020
Yesterday, the BBC ran a story with the factually untrue headline, “Cellebrite claimed to have cracked chat app’s encryption.” This is false. Not only can Cellebrite not break Signal encryption, but Cellebrite never even claimed to be able to.
Since we weren’t actually given the opportunity to comment in that story, we’re posting this to help to clarify things for anyone who may have seen the headline.
Adding Encrypted Group Calls to Signal
Signal on 14 Dec 2020
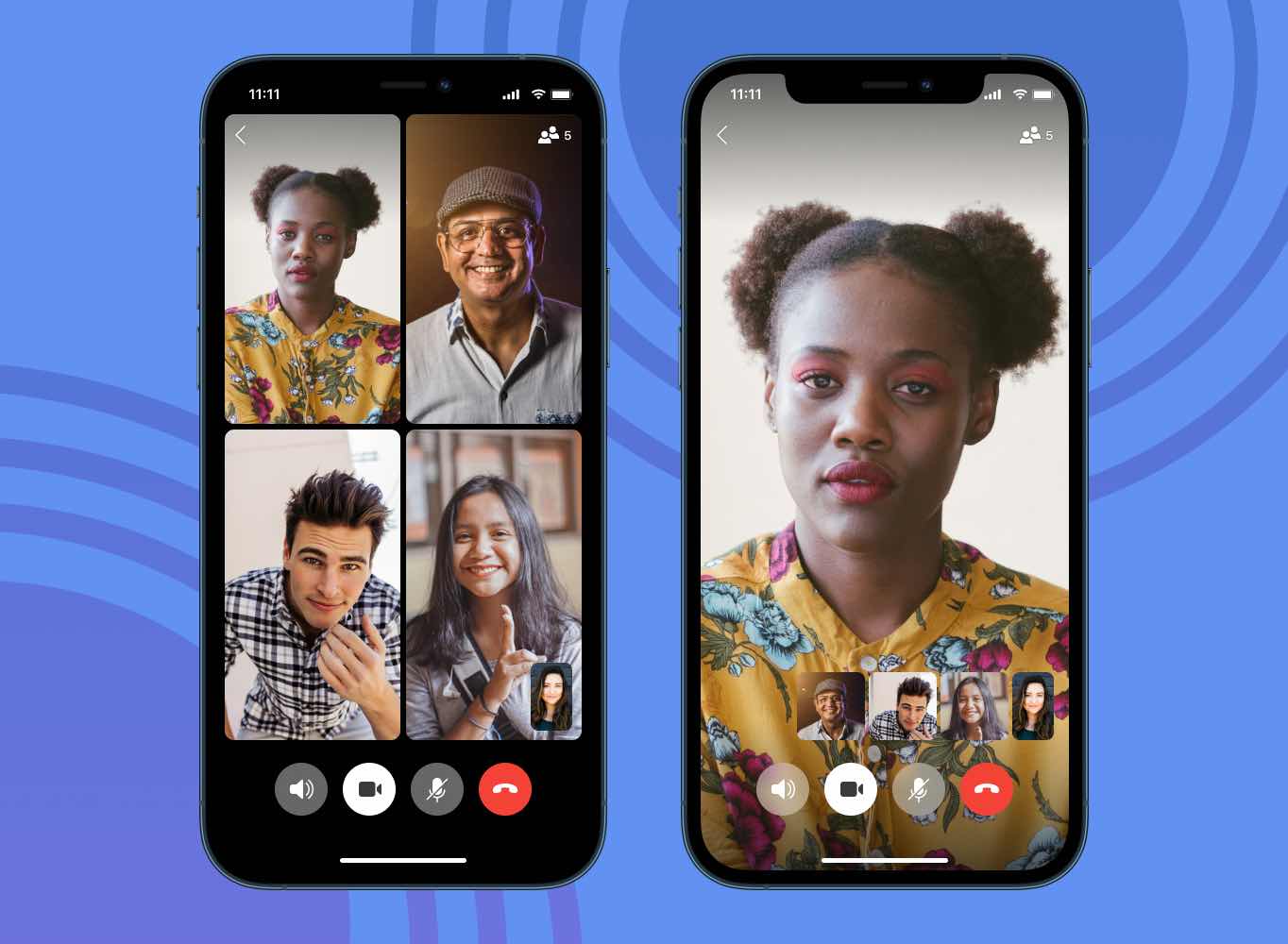
2020 has seen its fair number of challenges and changes. We’ve all adapted to new ways of staying in touch, getting work done, celebrating birthdays and weddings, and even exercising. As more and more of our critical and personal moments move online, we want to continue to provide you with new ways to share and connect privately.
Today, we’re launching group calls in Signal with the latest versions of our apps. Group calls are free, private, and end-to-end encrypted — like everything else on Signal.
Link Up with Group Links
Signal on 28 Oct 2020
We recently released a new version of Signal groups with group admins, @mentions, permissions, and more. Today we’re adding one more feature into the mix: group links, which let you quickly create a link that anyone can follow to join your group. Like our other new group features, you can create a new group to try it out now, but these features will be coming soon to your existing Signal groups.
Research on your terms
greggcorp on 26 Oct 2020
Signal has always benefitted from our engaged and supportive community, and wouldn’t be what it is without your input and feedback. As the number of people using Signal has grown, so have our efforts to keep pace with what people expect from a messaging app, and where we might find new opportunities for Signal.
Software companies typically overflow with data that explains the past and forecasts possible futures. They know exactly who is doing what with their products, how often, and where. While an abundance of data can contribute to their product and user experience decisions, these data collection practices are often rife with overreach and abuse. Signal doesn’t track you, collect your data, or measure which features you use. Anything and everything you do with Signal is your business. Which means that for us to dial in the features and experiences you expect calls for a respectful practice of research.
Multi-device calls with ICE forking
peter-signal on 20 Oct 2020

Now that voice and video calls are available for everyone on Signal Desktop and iPad, in addition to our mobile clients, we want to share a closer look at the technology that makes it possible for incoming calls to ring across multiple devices. Every call placed on Signal has always been private and end-to-end encrypted, but we previously supported only calls to or from one primary device per person. Now, you can make and receive secure audio and video calls from the devices in your pocket, on your lap, or at your desk.
New Features Coming to Signal Groups
Signal on 14 Oct 2020
Whether it’s staying in touch with family and friends, planning a party, scheduling an event, getting work done, or organizing for change, group chats are an increasingly important part of Signal. Today we’re releasing a new version of Signal groups that gives you a richer private group experience with group admins, granular permissions, @mentions and more. If you’re excited to try out these features now, you can create a new group to do so. These features will be coming soon to your existing Signal groups in a future update.
Signal groups are built on top of the new private group system technology we previewed last year, which gives you a modern group chat experience while keeping your groups private: the Signal service has no access to your group memberships, group titles, group avatars, or group attributes.
Update: This feature is now available in production.
The latest beta release of Signal Desktop includes preliminary support for one-to-one voice and video calls. Call your friends and family on macOS, Windows, and Linux; see their smiles on a larger screen; hear their laughter through the big speakers on your desk; and help us test the next generation of calling on Signal.
Beta users get an early chance to evaluate call quality and performance while we continue to improve the interface and work on upcoming features.
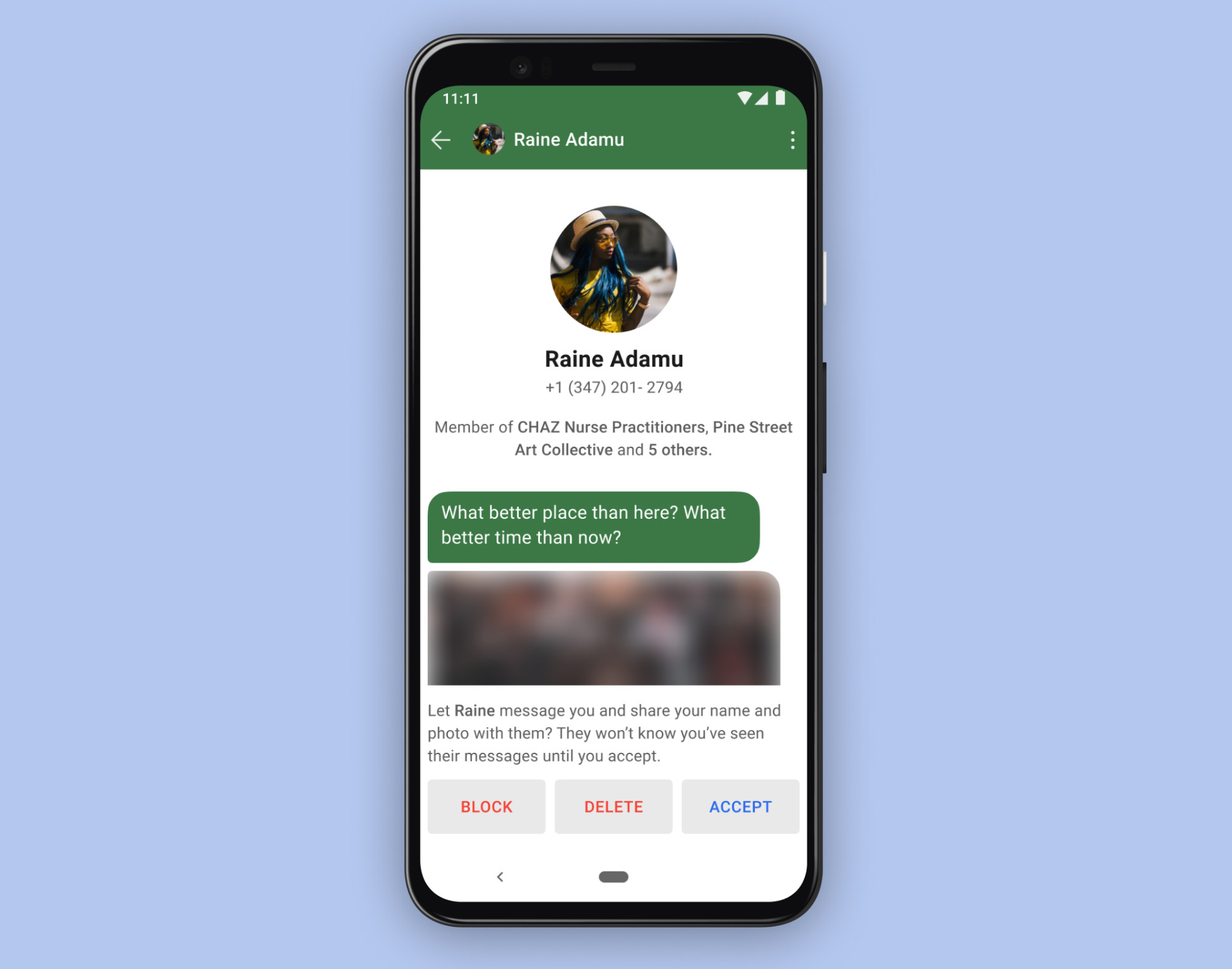
The number of people who join Signal every day is still growing at a record pace. With so many new conversations getting started, we’ve heard from a lot of users that they’d like more control over how they begin.
With message requests, when someone who isn’t in your contacts starts a new chat with you or adds you to a group, you can quickly see more info before accepting the request, deleting it, or blocking the conversation.
Certifiably "F"ine
jlund on 01 Jul 2020
Sometimes people dive into Signal’s code looking for domain names, and then they send us screenshots asking if they should be concerned:

We reply with a short explanation that lays out why there’s nothing wrong, but we understand the confusion. Nobody would be excited about getting a grade like this on a homework assignment – and you’d have to stay after class and ask the teacher what the hell a “T” even means on your report about summer vacation (“T”oo cool for school?).
Let’s take a deeper look at what’s going on.
Help us encrypt even more faces
junh3 on 23 Jun 2020
It’s been about two weeks since we announced an initiative to distribute versatile face coverings to help support everyone who is self-organizing for change in the streets. Since then, we’ve shipped over $25,000 worth of face coverings to organizers throughout the United States. Over $6,000 worth of merchandise was sent to Washington D.C. last week in time for the Juneteenth events in the heart of the city.
We continue to be inspired by the energy and enthusiasm that is helping to shape change in America, and many people have reached out and asked how they can help. In order to make it as easy as possible, we’re opening up a separate donation space to continue funding these efforts.
It's OK to be a little Emojional
jlund on 12 Jun 2020
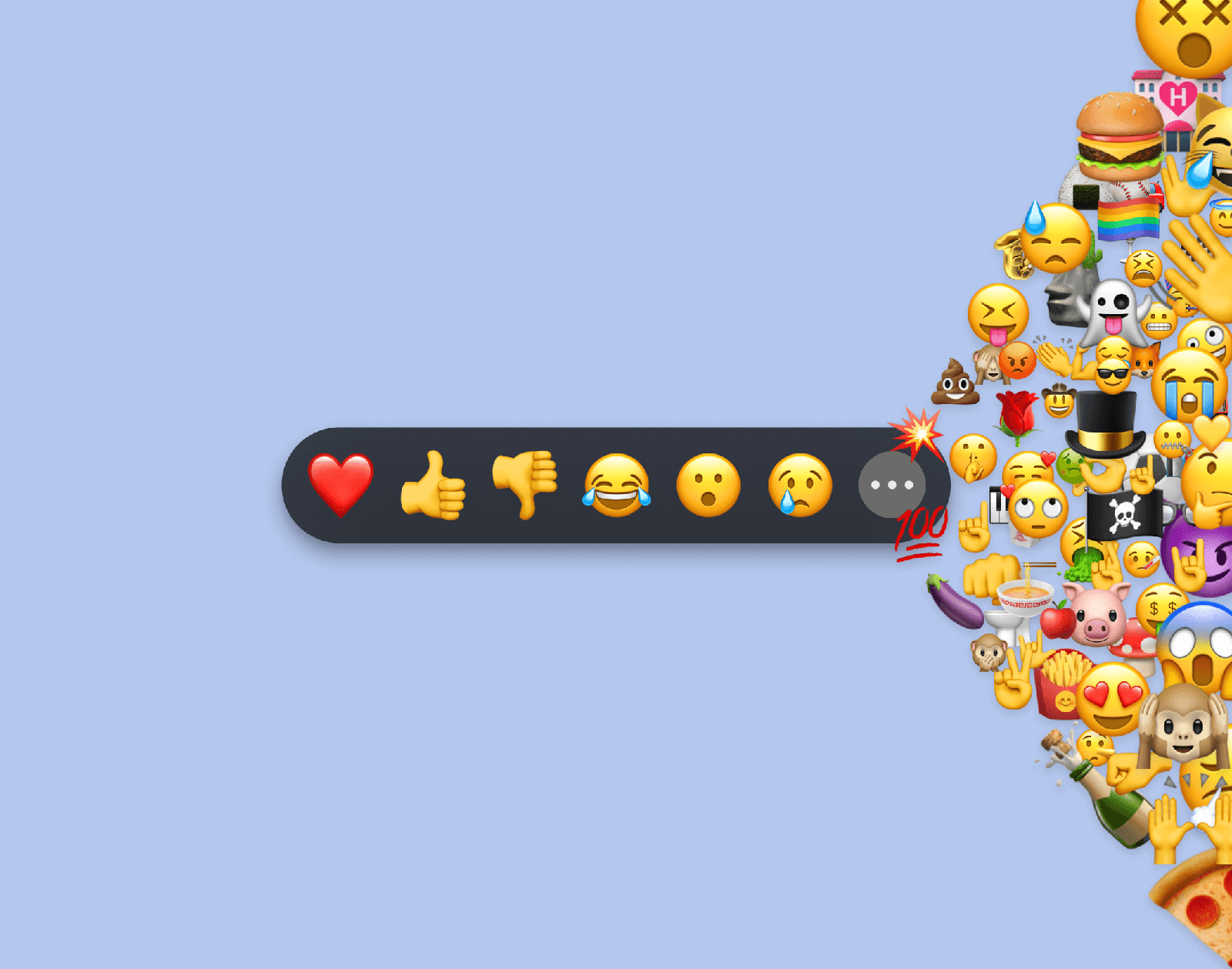
The world was a different place when we announced message reactions back in February, but expressing the way you feel has never been more important. Instead of being limited to the default set of reactions that we started with, the latest Signal updates for Android, Desktop, and iOS let you react with even more emoji.
Your next upgrade deserves an upgrade
imperiopolis on 09 Jun 2020
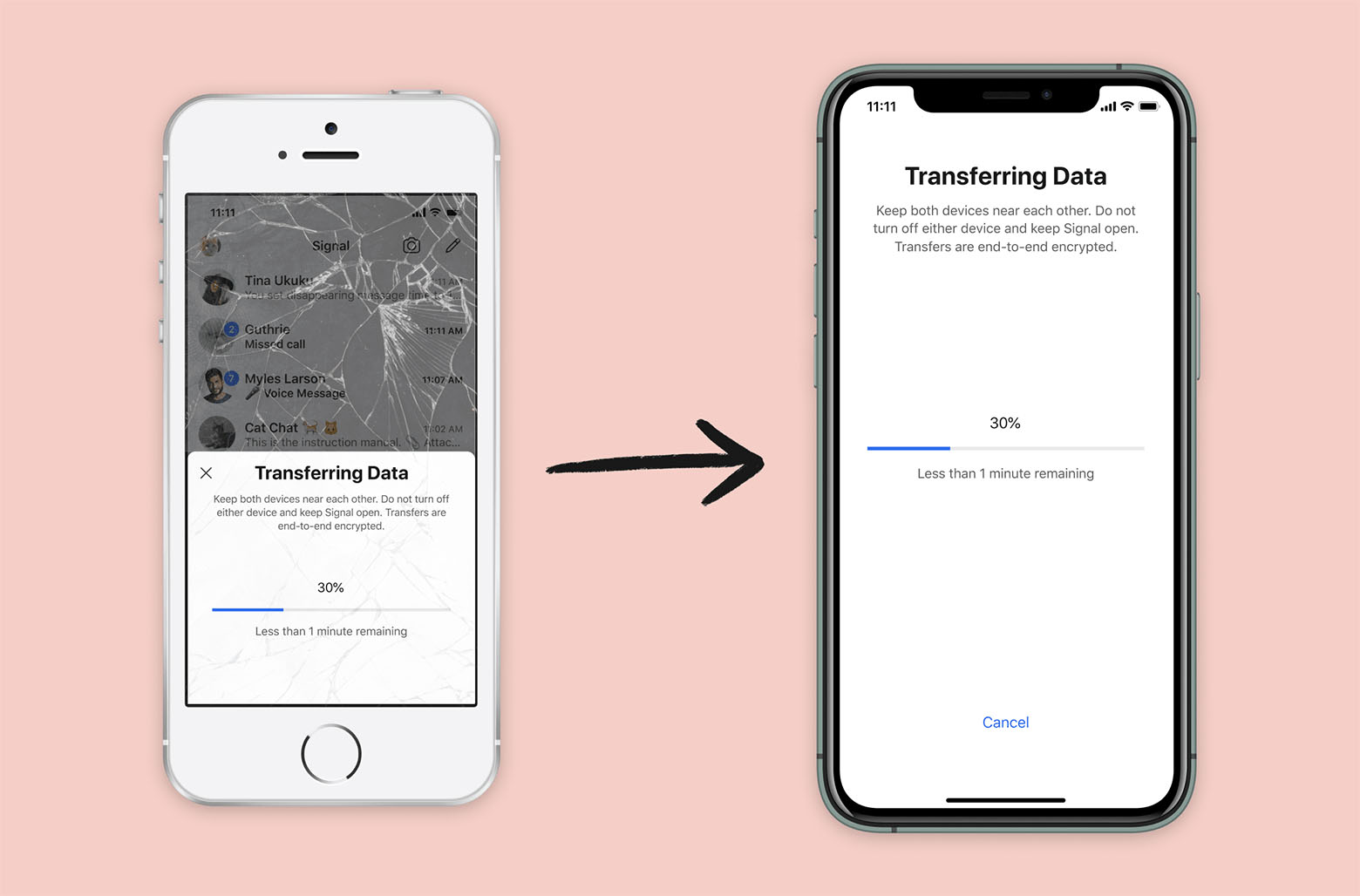
Signal iOS now includes a new feature that makes it possible to switch to a brand-new iPhone or iPad while securely transferring Signal information from your existing iOS device. As with every new Signal feature, the process is end-to-end encrypted and designed to protect your privacy. Transfers also occur over a local connection (similar to AirDrop), so even large migrations can be completed quickly.
Encrypt your face
junh3 on 08 Jun 2020

One immediate thing seems clear about 2020: it’s a good year to cover your face. Online, we’re working to scale and improve Signal for everyone that is relying on it, but as one small offline way to help support everyone self-organizing for change in the streets, we’re also distributing face coverings free of charge.
In the midst of world-wide protests against racism and police brutality, a lot of people are becoming more immediately aware and concerned about the security of their data and online communication. We’ve gotten a lot of questions at Signal over the past week, so we wanted to briefly recap how it is that we’ve designed Signal, and how we think about concepts like privacy, security, and trust.
Blur tools for Signal
moxie0 on 03 Jun 2020

Right now, people around the world are marching and protesting against racism and police brutality, outraged by the most recent police murders of George Floyd and Breonna Taylor. At Signal, we support the people who have gone into the streets to make their voices heard. We believe that something in America needs to change, and even if we don’t know exactly how, we support and trust in the people who are self-organizing around the country to figure it out.
Many of the people and groups who are organizing for that change are using Signal to communicate, and we’re working hard to keep up with the increased traffic. We’ve also been working to figure out additional ways we can support everyone in the street right now.
One immediate thing seems clear: 2020 is a pretty good year to cover your face.
Introducing Signal PINs
Signal on 19 May 2020
At Signal, our goal is to build a reliable, secure, and private communication experience that is broadly accessible and simple to use. From the beginning, we’ve designed Signal so that your information is in your hands rather than ours.
230, or not 230? That is the EARN IT question.
jlund on 08 Apr 2020
Over the past several weeks, Signal traffic has gone through the roof. New users are signing up at unprecedented rates, and we’ve expanded our server capacity faster than we ever anticipated.
It means a lot to us that so many people are relying on Signal during this difficult time. When users check in on their families, share moments of solace, smile with their friends, or discuss sensitive health issues with their doctors, Signal’s end-to-end encryption and privacy-preserving technology helps keep this information secure.
At a time when more people than ever are benefiting from these protections, the EARN IT bill proposed by the Senate Judiciary Committee threatens to put them at risk. COVID-19 has us sheltering in place, but we cannot quarantine our concerns.
Take a shortcut through keyboard history
jlund on 26 Feb 2020
Signal Artist Series: Two new sticker packs from Swoon
jlund on 11 Feb 2020
We announced support for stickers in Signal less than two months ago. Since then, over five thousand sticker packs have been uploaded. Today we are officially adding two more: Hands and Faces by Swoon.
Give reactions a thumbs up
jlund on 03 Feb 2020
When you’re standing next to a friend who says something funny, you can just laugh. You don’t need to pause and say “I found what you just said humorous” or quote their own words back to them before displaying a real-world emoji on your face. This feeling of immediacy and effortless response is what reactions are all about. They’re a quick way to share your take on any message, and you can try them today in the latest Signal beta.
Improving Registration Lock with Secure Value Recovery
jimio on 27 Jan 2020
Registration Lock allows you to set a PIN that is required for account registration in addition to standard SMS-based verification. Today’s Signal beta release enhances the security of these PINs by transitioning them to use Secure Value Recovery.
Storage management for Signal Android
alan-signal on 13 Jan 2020
Signal for Android now includes storage management functionality that helps visualize files across all of your conversations, sorted by size and type, in order to assist you in reducing the amount of space Signal uses on your device.
Sometimes once is better than a lifetime
jlund on 06 Jan 2020
Today’s beta releases of Signal for Android and iOS include a new way to send individual photos and videos that are automatically removed from a conversation thread after they have been viewed.
Technology Preview for secure value recovery
jlund on 19 Dec 2019
At Signal, we want to make privacy simple. From the beginning, we’ve designed Signal so that your information is in your hands rather than ours. Technologies like Signal Protocol secure your messages so that they are never visible by anyone but you and the intended recipients. Technologies like private contact discovery, private groups, and sealed sender mean that we don’t have a plaintext record of your contacts, social graph, profile name, location, group memberships, groups titles, group avatars, group attributes, or who is messaging whom. Plaintext databases have never been our style. We don’t want to build a system where you trust us with your data; we want to build a system where you don’t have to.
We’ve been working on new techniques based on secure enclaves and key splitting that are designed to enhance and expand general capabilities for private cloud storage. Our aim is to unlock new possibilities and new functionality within Signal which require cross-platform long-term durable state, while verifiably keeping this state inaccessible to everyone but the user who created it.
Make privacy stick
jlund on 17 Dec 2019
They get slapped on street signs. We wear them on our clothes to identify ourselves to distant coworkers during awkward holiday parties. Some people create massive galleries on their laptops in overlapping levels stacked so deep that the hinges begin to lose their structural integrity and LCD screens struggle to remain upright. The digital versions are even more popular, and we get asked about them a lot.
Stickers are everywhere, and now they’re in Signal too. They’re a fun way to add a new layer of expression to your conversations – and just like every other Signal feature, they are also encrypted, private, and secure.
Technology Preview: Signal Private Group System
jimio on 09 Dec 2019
Groups are inherently social, and Signal is a social app. Whether you’re planning a surprise party, discussing last night’s book club meeting, exchanging photos with your family, or organizing something important, group messaging has always been a key feature of Signal.
Signal provides private groups: the Signal service has no record of your group memberships, group titles, group avatars, or group attributes. We’ve been working on new private group technology that will enable group administrators and access control, improve group scalability, and set the stage for a much richer group experience – all while maintaining Signal’s unique group security and privacy properties. We’re moving into the future while keeping what we loved about the past.
Signal for iPad, and other iOS improvements
jlund on 27 Nov 2019
Signal 3.0 is now available in the App Store:
- iPad support has arrived. Set up your favorite tablet as a linked device.
- Forward messages between threads. Editing support lets you amend, extend, append, explain what you intend, or tie up loose ends before you hit send.
- Built-in support for video trimming can help any clip turn into a highlight.
- Tap on someone’s avatar in a group conversation to quickly message or call them. While the group agonizes over dinner plans, subtly exert your influence by making a case for your favorite restaurant in one-on-one conversations.
- Jump between threads and survey your message landscape (in landscape) with a horizontal inbox/conversation view on larger devices.
We would like to thank all of the alpha and beta users who helped us test and stabilize this release. If you want to get an early preview of new Signal features, you can join the beta community here.
I link therefore I am
jlund on 06 Feb 2019
The latest releases of Signal for Android, Desktop, and iOS are rolling out now with the ability to send optional link previews. This feature is built on the same foundation that has powered Signal’s animated GIF search for more than two years and that we have since expanded with additional privacy enhancements.
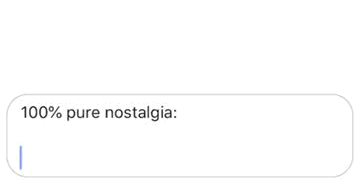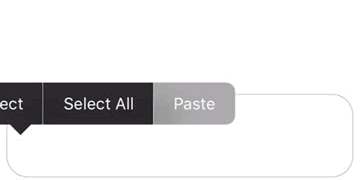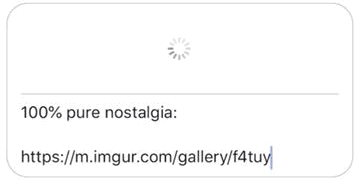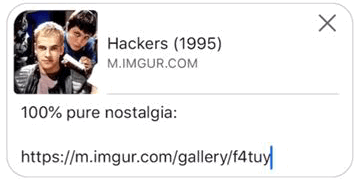
We’re launching link previews with initial support for Imgur, Instagram, Reddit, and YouTube. These are four of the most popular sites on the Internet and their heavy focus on visual content makes them a perfect fit for this feature. We don’t believe that privacy is about austerity, and now Signal users can see what’s behind the URL while sharing this content with their friends.
Setback in the outback
jlund on 13 Dec 2018
Like many others, we have been following the latest developments in Australia related to the “Assistance and Access” bill with a growing sense of frustration. The widespread adoption of strong cryptography and end-to-end encryption has given people around the world the ability to protect their personal information and communicate securely. Life is increasingly lived online, and the everyday actions of billions of people depend on this foundation remaining strong.
Attempting to roll back the clock on security improvements which have massively benefited Australia and the entire global community is a disappointing development.
Technology preview: Sealed sender for Signal
jlund on 29 Oct 2018
In addition to the end-to-end encryption that protects every Signal message, the Signal service is designed to minimize the data that is retained about Signal users. By design, it does not store a record of your contacts, social graph, conversation list, location, user avatar, user profile name, group memberships, group titles, or group avatars.
We have been exploring techniques to further reduce the amount of information that is accessible to the service, and the latest beta release includes changes designed to move Signal incrementally closer to the goal of hiding another piece of metadata: who is messaging whom.
A letter from Amazon
moxie0 on 01 May 2018
Last week, we received the following email from Amazon:
From: [redacted], [redacted] <[redacted]@amazon.com>
Subject: Notification of potential account suspension regarding AWS Service Terms
Moxie,
Yesterday AWS became aware of your GitHub and Hacker News/ycombinator posts describing how Signal plans to make its traffic look like traffic from another site, (popularly known as “domain fronting”) by using a domain owned by Amazon -- Souq.com. You do not have permission from Amazon to use Souq.com for any purpose. Any use of Souq.com or any other domain to masquerade as another entity without express permission of the domain owner is in clear violation of the AWS Service Terms (Amazon CloudFront, Sec. 2.1: “You must own or have all necessary rights to use any domain name or SSL certificate that you use in conjunction with Amazon CloudFront”). It is also a violation of our Acceptable Use Policy by falsifying the origin of traffic and the unauthorized use of a domain.
We are happy for you to use AWS Services, but you must comply with our Service Terms. We will immediately suspend your use of CloudFront if you use third party domains without their permission to masquerade as that third party.
Thank you,
[redacted]
General Manager, Amazon CloudFront
Signal Foundation
moxie0 on 21 Feb 2018
Long before we knew that it would be called Signal, we knew what we wanted it to be. Instead of teaching the rest of the world cryptography, we wanted to see if we could develop cryptography that worked for the rest of the world. At the time, the industry consensus was largely that encryption and cryptography would remain unusable, but we started Signal with the idea that private communication could be simple.
Since then, we’ve made some progress. We’ve built a service used by millions, and software used by billions. The stories that make it back to us and keep us going are the stories of people discovering each other in moments where they found they could speak freely over Signal, of people falling in love over Signal, of people organizing ambitious plans over Signal. When we ask friends who at their workplace is on Signal and they respond “every C-level executive, and the kitchen staff.” When we receive a subpoena for user data and have nothing to send back but a blank sheet of paper. When we catch that glimpse of “Signal blue” on a metro commuter’s phone and smile.
In collaboration with Signal, Microsoft is introducing a Private Conversations feature in Skype, powered by Signal Protocol.
Expanding Signal GIF search
jlund on 01 Nov 2017
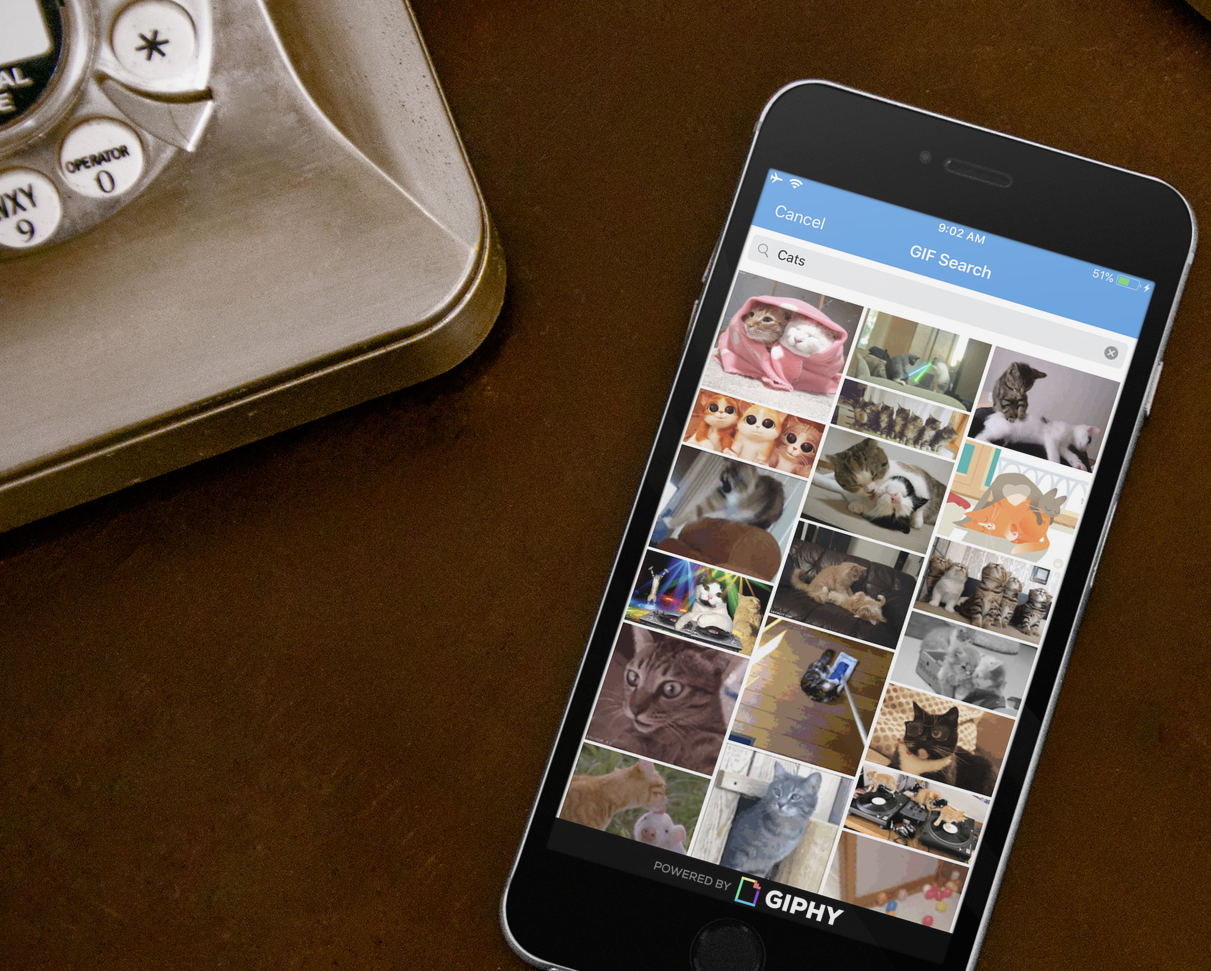
Today’s Signal beta for iOS includes support for animated GIF search. Signal iOS has long supported sending and receiving GIFs, but today’s beta adds support for browsing and searching popular GIFs from within Signal.
We previously announced experimental support for animated GIF search in Signal Android, which we’re now bringing to iOS, along with some privacy updates to the process.
Standalone Signal Desktop
scottnonnenberg on 31 Oct 2017
Signal Desktop is now available in a new, standalone form, and the Chrome App has been deprecated.
Read receipts are coming to Signal
jlund on 03 Oct 2017
Today’s beta release of Signal for Android and iOS includes support for read receipts. This is an optional new feature that gives you the ability to see and share when messages have been read. Something tells us that you might find this useful…
Technology preview: Private contact discovery for Signal
moxie0 on 26 Sep 2017
At Signal, we’ve been thinking about the difficulty of private contact discovery for a long time. We’ve been working on strategies to improve our current design, and today we’ve published a new private contact discovery service.
Using this service, Signal clients will be able to efficiently and scalably determine whether the contacts in their address book are Signal users without revealing the contacts in their address book to the Signal service.
Encrypted profiles for Signal now in public beta
jlund on 06 Sep 2017

The latest Signal beta for Android and iOS introduces support for Signal Profiles.
Profiles allow you to add a picture and display name that will be shown alongside your existing phone number when communicating with other users. Conversations will feel more personal. Group threads will be less confusing.
All of this is possible without sacrificing the privacy and security that you have come to expect from Signal.
Safety number updates
moxie0 on 16 Jun 2017
The latest Signal beta includes some changes to the way safety numbers work. Back in November, we introduced experimental support for “advisory” safety number changes, with the objective of collecting feedback in order to eventually make this the default experience.
We’ve taken the feedback we’ve received over the past six months and incorporated it into a set of changes that we’re releasing into beta today.
Video calls for Signal out of beta
moxie0 on 13 Mar 2017

We recently released encrypted video calling as an opt-in beta. We’ve spent the past month collecting feedback and addressing the issues that the Signal community found in order to get it ready for production. Today’s Signal release for Android and iOS enables support for end-to-end encrypted video calls by default, which also greatly enhances the quality of Signal voice calls as well.
We think it’s a big improvement, and hope you will to.
Video calls for Signal now in public beta
moxie0 on 14 Feb 2017
Today’s Signal release for Android and iOS includes beta support for video calls.
This represents an entirely new calling infrastructure for Signal, and should increase voice call quality as well. We think it’s a big improvement, but we’re rolling it out in stages to collect feedback from people with different devices, networks, and regions in order to ensure there are no surprises when it’s enabled for everyone by default.
To help us test on Android and iOS, toggle Signal Settings -> Advanced -> Video calling beta.
Only calls between Signal users who have both enabled the video calling beta will use the new calling system.
There is no WhatsApp 'backdoor'
moxie0 on 13 Jan 2017
Today, The Guardian published a story falsely claiming that WhatsApp’s end-to-end encryption contains a “backdoor.”
The latest Signal for Android release includes support for adding doodles, stickers, and text to images.
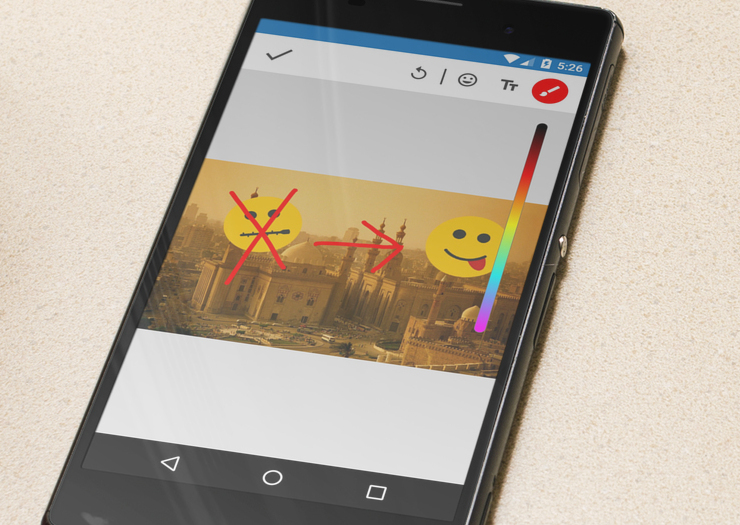
This release also includes support for censorship circumvention in Egypt and the United Arab Emirates.
Safety number updates
moxie0 on 17 Nov 2016
The latest Signal release includes some changes to the way safety numbers work.
Safety numbers allow Signal users to verify the privacy of their communication with a contact, either by comparing a number or by scanning a single QR code. We recently introduced this new design as an update to Signal’s previous UX, which we felt was no longer adequate for what people had come to expect from Signal. Let’s look at the safety numbers design in more detail, then go over what’s new in this release.
Signal and GIPHY
moxie0 on 01 Nov 2016
The latest Signal release for Android includes support for GIF search and browsing. Signal has long supported sending and receiving GIFs, but this is an experiment that allows users to browse, search, and select popular GIFs from within Signal.
Disappearing messages for Signal
moxie0 on 11 Oct 2016
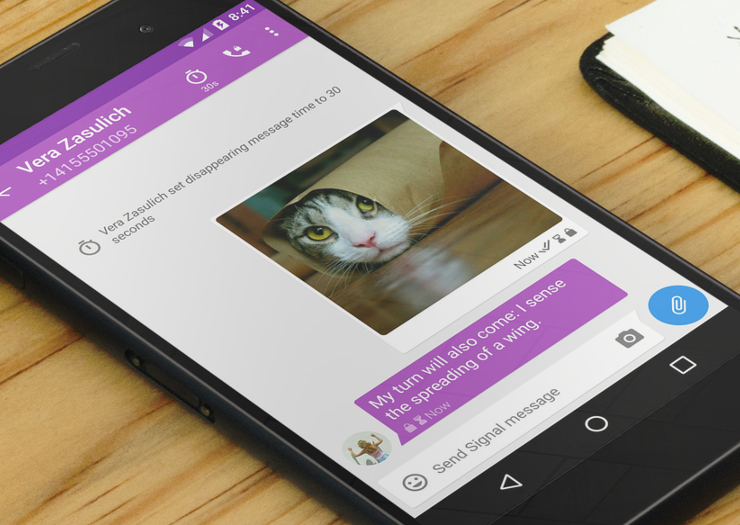
The latest Signal release for iPhone, Android, and Desktop now includes support for disappearing messages.
The timer has come
With this update, any conversation can be configured to delete sent and received messages after a specified interval. The configuration applies to all parties of a conversation, and the clock starts ticking for each recipient once they’ve read their copy of the message.
Desktop support comes to Signal for iPhone
moxie0 on 26 Sep 2016

The latest Signal for iPhone release now includes multi-device support, allowing you to seamlessly move your private messaging experience from your iPhone to your desktop computer and back. Once you’ve linked a desktop client from within the Signal iPhone app, you can switch to the desktop at any time, whether your phone is online or not.
The Signal Desktop app also supports a new iOS theme, which is enabled by default whenever you link a desktop client from the Signal iPhone app. Try it out!
Signal for Android Attachment Bug
moxie0 on 20 Sep 2016
We recently received a great bug report from Jean-Philippe Aumasson and Markus Vervier, who identified a problem with the way that image, audio, and video attachments are processed by the Signal for Android code. We consider the implications of the bug to be low risk to Signal users, but have released an update for the Signal Android app that addresses the problems they reported.
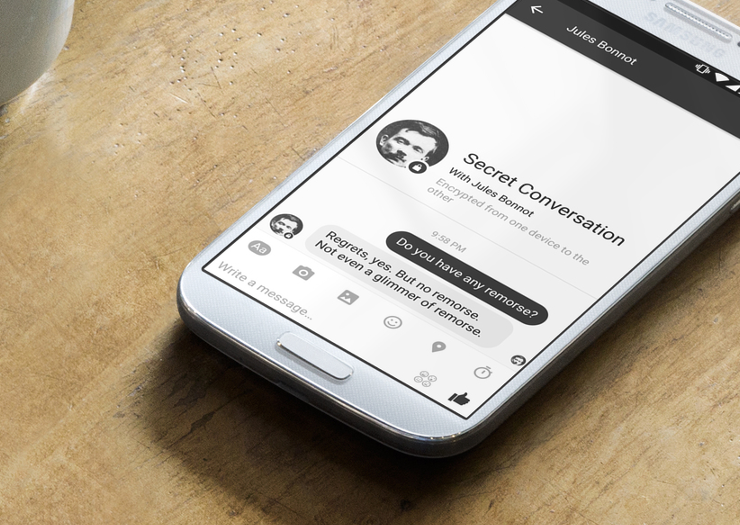
Facebook Messenger has started rolling out Secret Conversations, a feature that enables end-to-end encryption for conversations within Messenger. Secret Conversations is built on Signal Protocol, a modern, open source, strong encryption protocol we developed for asynchronous messaging systems.
License update
moxie0 on 13 Jun 2016
Signal Protocol is a modern, open source, strong encryption protocol for asynchronous messaging systems. We use Signal Protocol as the foundation for our own private messaging app, Signal, but also make Signal Protocol libraries available for other applications to use.
Our Signal Protocol libraries are open source, licensed GPLv3. We like the GPL for the quality control that it provides. If someone publicly says that they’re using our software, we want to see if they’ve made any modifications, and whether they’re using it correctly. This helps to increase transparency and accountability in deployments of our software, which we feel are important for end-to-end encryption.
At Open Whisper Systems, our goal is to make private communication simple. The foundation of our technology is Signal Protocol, a modern, open source, strong encryption protocol for asynchronous messaging systems. It is built from the ground up to make seamless end-to-end encrypted messaging possible.
Reflections: The ecosystem is moving
moxie0 on 10 May 2016
At Open Whisper Systems, we’ve been developing open source “consumer-facing” software for the past four years. We want to share some of the things we’ve learned while doing it.
As a software developer, I envy writers, musicians, and filmmakers. Unlike software, when they create something, it is really done — forever. A recorded album can be just the same 20 years later, but software has to change.
Software exists as part of an ecosystem, and the ecosystem is moving. The platform changes out from under it, the networks evolve, security threats and countermeasures are in constant shift, and the collective UX language rarely sits still. As more money, time, and focus has gone into the ecosystem, the faster the whole thing has begun to travel.
All of this means that the set of expectations users have for social and communication features are evolving rapidly. Anyone building software today knows that it is not possible to stand still.
Signal Desktop beta now publicly available
liliakai on 07 Apr 2016
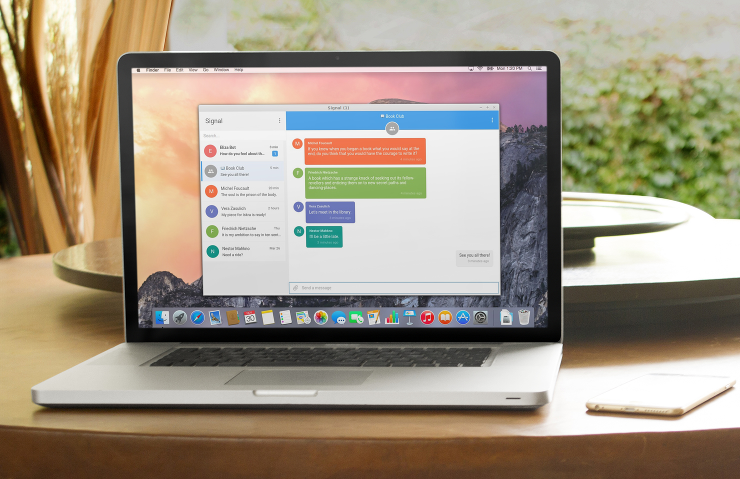
For the past few months, the Signal Desktop beta has been available through an invitation program. We’ve gotten a lot of feedback, made a lot of improvements, and are now ready to open the beta up for public access.
WhatsApp's Signal Protocol integration is now complete
moxie0 on 05 Apr 2016

At Open Whisper Systems, our goal is to make private communication simple. A year ago, we announced a partnership with WhatsApp and committed to integrating the Signal Protocol into their product, moving towards full end-to-end encryption for all of their users by default.
Over the past year, we’ve been progressively rolling out Signal Protocol support for all WhatsApp communication across all WhatsApp clients. This includes chats, group chats, attachments, voice notes, and voice calls across Android, iPhone, Windows Phone, Nokia S40, Nokia S60, Blackberry, and BB10.
As of today, the integration is fully complete. Users running the most recent versions of WhatsApp on any platform now get full end-to-end encryption for every message they send and every WhatsApp call they make when communicating with each other. This includes all the benefits of the Signal Protocol – a modern, open source, forward secure, strong encryption protocol for asynchronous messaging systems, designed to make end-to-end encrypted messaging as seamless as possible.
Reproducible Signal builds for Android
moxie0 on 31 Mar 2016
As of our latest Android release, Signal builds are reproducible. Reproducible builds help to verify that the source code in our GitHub repository is the exact source code used to build the compiled Signal APK being distributed through Google Play.
Signal on the outside, Signal on the inside
moxie0 on 30 Mar 2016
A few months ago we completed the process of unifying all of our apps across Android, iOS, and the Desktop under the name ‘Signal.’ This simplified the language around our apps and eliminated a lot of confusion. Now we’re doing the same thing “inside” our apps by renaming Axolotl to Signal Protocol.
Axolotl has been the name of the cryptographic protocol that our apps use for end-to-end encryption, but it’s not the easiest word to pronounce. Sometimes people use ‘Axolotl’ to refer to just the base double ratchet instead of the full messaging protocol, so there has also been some confusion around what people mean when they say ‘Axolotl.’
To continue eliminating confusion and simplifying everything within the Signal ecosystem, we’re renaming Axolotl to Signal Protocol. The implementations have been renamed, so there are open source Signal Protocol libraries available for C, Objective C, Java, and JavaScript in our GitHub repository, as before. These have been making their way into an increasing number of communication apps, and we’re excited for the future of the Signal Protocol as it continues to spread.
Signal Desktop
moxie0 on 02 Dec 2015
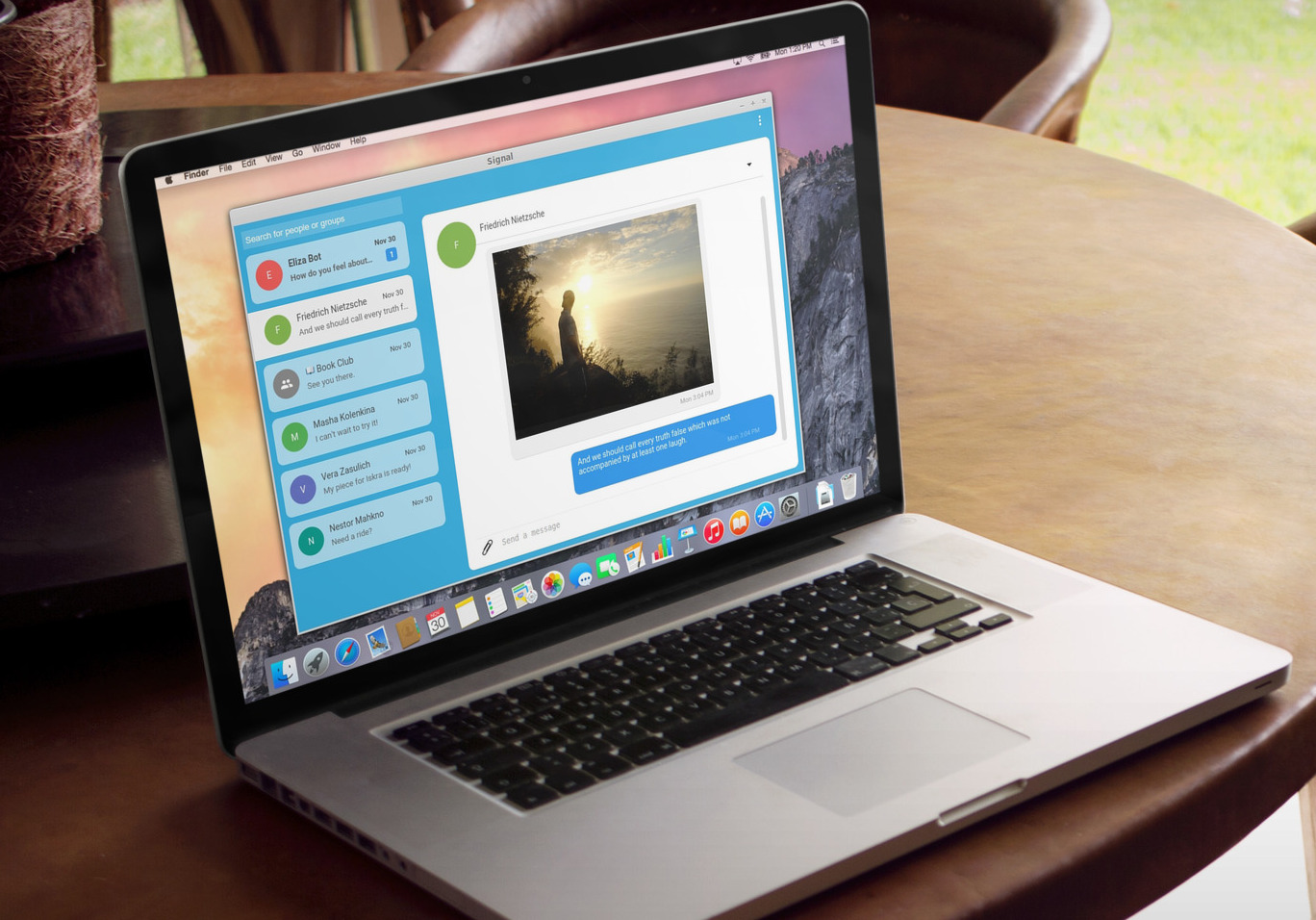
Today we’re making the Signal Desktop beta available. Signal Desktop brings the trusted private messaging experience of Signal to the desktop, with a simplicity that allows you to seamlessly continue conversations back and forth between your mobile device and your desktop computer.
Just Signal
moxie0 on 02 Nov 2015
Today we’ve started rolling out Signal for Android, which unites simple private messaging and simple private calling into a single app on Android. This is the culmination of our effort to combine TextSecure and RedPhone into one app, which we began on iPhone and are now bringing to completion on Android.
No Risk No Reward
riyapenn on 18 Aug 2015
After immersing myself for years and years in the world of finance (specifically, options market making and algorithmic trading), there was no escaping this mantra of “no risk, no reward.” Most of the time, my (trading) style was fairly risk-averse. I knew how to find the signals of opportunities among the daily noise to reap small rewards. Fortunately, I also learned how to think about the outliers and to take the occasional big but calculated risks.
Saying goodbye to encrypted SMS/MMS
moxie0 on 06 Mar 2015
It’s 2015, and the end of the road for encrypted SMS/MMS in TextSecure.
The TextSecure story started back in 2009, at the dawn of the smartphone era. Back then, TextSecure focused on securing the transport that everyone coming from feature phones was familiar with: SMS. Today, many things have changed, and TextSecure now emphasizes the “TextSecure transport,” which uses data rather than SMS. While we remain committed to supporting plaintext SMS/MMS in addition to the encrypted TextSecure transport so that the app can function as a unified messenger, we are beginning the process of phasing out support for SMS/MMS as an encrypted transport in favor of the TextSecure data protocol.
Signal 2.0: Private messaging comes to the iPhone
moxie0 on 02 Mar 2015
Today we’re releasing Signal 2.0, with support for TextSecure private messaging.
It is now possible to send end-to-end encrypted group, text, picture, and video messages between Signal on iPhone and TextSecure on Android, all without SMS and MMS fees. Signal 2.0 blends private phone calls and private messaging into a single frictionless interface, allowing you to focus on what’s important by quickly organizing your conversations using an inbox/archive work flow.
Beyond the Grunts and Clicks: An Exploration into Doing Things the Hard Way
A guest post by greggawatt on 31 Jan 2015
Winter Break Of Code Day Nineteen

I recently had the opportunity to listen to another amazing podcast from 99% Invisible, a program about “design, architecture and the 99% invisible activity that shapes our world.” It got me thinking about how my world is shaped by the way I engage with computers. The podcast is a story about a computer scientist named Doug Engelbart who was, in essence, a crazy brilliant genius. He thought of ways to change how we interacted with computers and, most famously, was the inventor of the computer mouse. He also invented a specialized companion device to the mouse that worked like the one-hand equivalent of a keyboard.
Paddle Out
A guest post by lconnolly on 30 Jan 2015
Winter Break Of Code Day Eighteen

Late this afternoon I took a break from working to surf. The sun was setting and a cool breeze was picking up as grey clouds billowed behind the mountains along Hanalei Bay. I had spent most of the day wrangling content, markup, and CSS, and the Pacific was calling. There was still plenty of work to be done, but balance is important, and my mind needed to reset. Surfing would be today’s lesson.
Winter Break Of Code Day Seventeen

In this life nearly every relationship we create and maintain is built upon expectations. You do this, I’ll do that, and together we’ll fail to oppose entropy but stand a chance at plotting and navigating a loose course through it. These expectations extend beyond the individual, past the family, and onto society.
Naked
on 28 Jan 2015
A post from Natalie, Winter Break Of Code, Day Sixteen
Today, I watched sunlight dance atop billowing waves, a natural circus spectacular.
I meditated on two syllables, allowing my breath and heartbeat to synchronize, and I too became a part of the show.
Winter Break Of Code, Day Fifteen
The 1988 film They Live is one of the last great masterpieces to come out of the Hollywood left. In the film, a drifter named John Nada discovers a box of sunglasses that, when worn, allows the wearer to really see the world around him.
For instance, when wearing the glasses, simple advertisements for consumer products are revealed as something other than what they appear.

Real World Kauai
A guest post by kmonkeyjam on 26 Jan 2015
Winter Break Of Code Day Fourteen
When I agreed to take part in Winter Break of Code, I had no idea what to really expect. While many people questioned my choice to spend my winter vacation writing code, I was excited for the opportunity to spend a week hanging out with an eclectic group of people while doing two of my favorite things: coding and surfing.

There's no you in srveillance
jlund on 25 Jan 2015
Winter Break Of Code Day Thirteen
My ten-year-old mind was completely blown when I realized that I could eavesdrop on the walkie-talkie conversations of the other kids in my neighborhood. I rode my bike to the library in stunned silence, found a book about codes and puzzles, and raced home to my computer. I reluctantly transformed QBasic into something other than a conduit for modified games of NIBBLES.BAS and GORILLA.BAS, and wrote a Caesar cipher implementation that worked in both directions. That ended up being the easy part.
Winter Break Of Code Day Twelve

A few days ago, someone suggested that we go scuba diving and I said “yeah sure, that sounds fun”. Once we actually got to the dive site I realized I had no clue what I signed up for. I was scared out of my fucking mind, squirming against the ocean’s currents, and convinced I would have to go back to shore while everyone else had fun since I was too much of a wuss. It took some time and a fair amount of patience from my dive instructor before I even made it underwater. But once I reached the calm depths of the ocean, I went from frantically holding my instructor’s hand to feeling comfortable exploring the reefs on my own. Instead of feeling disoriented by being underwater, it began to feel natural to swim among tropical fish and sea turtles.
Aloha But Not
A guest post by jackflips on 23 Jan 2015
Winter Break Of Code Day Eleven
Every morning at standup I’d watch the knife spin in slow motion, dread filling my chest and a voice in my head repeating, over and over, “not Slytherin.” (The target of the knife is the author of the next day’s blog post). I wasn’t sure that I could find new ways to marvel at the wonderful absurdity of stepping on a plane and trading reality for this – a chance to work on the world with a group of people that I’ve only admired from afar. I wasn’t sure that I had anything to say that hadn’t already been said by my new friends.
For the Love of Humans and Technology
A guest post by uxyoko on 22 Jan 2015
Winter Break of Code Day Ten
A couple of days ago, Jake, one of the brilliant full-timers on Open Whisper Systems, looked up from his laptop and asked me with a smile, “So, Yoko, what’s your life story? How did you come to love humans so much?” It was a whimsical way of asking why I do what I do and why I am here. Having studied Human Computer Interaction and being a user experience (UX) designer, I’ve been asked variations of this question many times before. But it was on this trip I realized my answer needs a little probing.
The pool on the roof must have a leak
rileyjshaw on 21 Jan 2015
Winter Break Of Code Day 9
Today we hiked the Kalalau Trail and swam beneath the cold spray of a waterfall.
Today we discussed the finer points of the axolotl protocol used by TextSecure.
Today we delighted in “shave ice”, a local delicacy that is definitely not a snow cone.
Today we wrote copy, polished features, closed bugs, and merged pull requests.
Measured by lines of code, today was short. Measured by steps taken, it was tall. Measured by ideas discussed, things learned, and sights seen, it was towering.

Encryption, encryption everywhere
A guest post by jessysaurusrex on 20 Jan 2015
Winter Break Of Code Day 8

A few weeks ago, an email full of information to help prep for Winter Break of Code popped up in my inbox. Throughout my personal countdown to the day I got to leave San Francisco for Hawaii, one line from that email continuously resonated throughout my mind: “Have your development environment ready to go.”
A curve by any other name
liliakai on 19 Jan 2015
Winter Break Of Code Day 7
Yesterday was a day of meetings. Discussion and debate flourished. Conversations ranged over all parts of every project. Words spoken aloud may have outnumbered lines of code shipped. The entire team was fully engaged and people nearly had to be dragged out of the house for an afternoon hike to the top of the ridge.

Despite our intense collective focus on conceptual progress, when Trevor agreed to present an overview of elliptic curve cryptography, the entire team, veterans and “li’l Whisperers” alike, fell silent and gathered ‘round the whiteboard.
We learned about fields and curves and groups, of basepoints and cofactors, secrets and signatures. Questions abounded and Trevor delivered the answers, one after another, albeit with enough handwaving that I thought he might lift off and fly himself back to the mainland. However, there was one question that even he could not answer: Why are they called elliptic curves?
From Weierstrass to Montgomery to Edwards formats, these geometric objects that form the essential mathematical underpinnings of many modern crypto systems are not defined by ellipses, nor do they resemble ellipses. Not even for very stretchy definitions of an ellipse. There is no immediately obvious connection. So why do we call them that?
As usual, to understand the universe, we must first bake an apple pie from scratch. Or at least pretend to.
The View From here
trevp on 18 Jan 2015
Winter Break Of Code, Day 6
I’ve been working with Open Whisper Systems on TextSecure for about a year and a half. I feel like I’ve earned better treatment than being forced to blog at knifepoint, but here we are, so I’ll tell my story.
Surrendering to the Potential of Constraints
abolishme on 17 Jan 2015
Winter Break Of Code, Day 5
The prophetic discourse of the Karai can be summed up in an observation and a promise: on the one hand, they constantly affirmed the fundamentally evil character of the world, on the other, they insisted that conquest of a good world was possible. “The world is evil! The world is ugly!” they said. “Let us abandon it!” they concluded. […] In short, it was not the discourse of the prophets that was unhealthy, but indeed, the world in which they spoke, the society in which they lived.
– Archeology of Violence, Pierre Clastres
At the peak of the Soviet Union’s civic society, more than five-hundred thousand Soviets belonged to a complex, almost ecological system of bureaucracy known as the Nomenklatura. Itself a reference to the Roman ‘list of names’ – a codified taxonomy into which people could be organized and signified – the Soviet government was built and constrained through social proximity.
The initial idea was to institute a horizontal decision-making system. A methodology that could define and populate thousands of roles for the collaborative administration of social order: ministers of industry, pedagogy, natural resources, foreign relations, internal affairs, communications, and so on.
It was a form of governance intended to gradually flatten a hierarchy that the early industrial revolution had exaggerated. However, over time the mechanics revealed – somewhat conversely – a total institutionalization of ‘nepotism’. Certain senior members of the Nomenklatura had the privilege to appoint new members, and maintain long lists of qualified candidates. New members, now obliged from a favor, formed allegiances to their patrons. Patrons themselves carried social debts to those who appointed them, and it went on like this up the stack into the inner circle. The hierarchy didn’t flatten, it sharpened.
Speed ahead to our modern life. My social relations are all but completely virtualized. My list of friends and followers, contacts and matches, profiles and handles … all thrum wildly. Apps are released every week which impose and constrain my lists into new formations, reconstructing my social life over and over. It’s possible to see the reflection of Soviet governance in our own lives today; perhaps there are hundreds of thousands of members (less, probably) of a new bureaucratic class – technocratic knowledge workers, let’s say – who organize and signify civic life in the contemporary age. Building cooperative protocols and APIs and apps and networks. Designing the interfaces and behaviors and experiences of everyone else. Teaching but sometimes refusing to learn, giving generously but sometimes taking without permission, anticipating what we want but often supposing what we want without asking. Designing our dismal fate. Slowly appointing their heirs by proximity.
As a publisher and designer, I count myself among this degenerate few and tread carefully whenever I manage to move or speak at all.
Signal to Noise
corbett on 16 Jan 2015
Winter Break Of Code Day 4
I’m not sure those attending their first break of code know what they are getting into. When I said “sure” to Moxie my first break, I sure didn’t. During that week I had already come to the conclusion “I have to see this (TextSecure iOS) through”. In the intervening time, I’ve become an expert on the Axolotl protocol, come to understand ZRTP, picked up the world’s best collaborator, helped with the final polish of Signal with RedPhone support and contributed a lot of code to the TextSecure prototype.
Third Day Of Code
TheBlueMatt on 15 Jan 2015
Winter Break Of Code Day 3
As it does every morning, the day started with Moxie singing the stand-up song, reminding us all (and waking up the slackers) that at 9am sharp we all get in a circle to discuss what we accomplished the day before and what our priorities are for the coming day.
Star Quality
elchao96 on 14 Jan 2015
Winter Break Of Code Day 2
Because I might get sappy, here’s a picture to ease that before I let it all out.

After being promptly woken up by numerous roosters at 7:30 AM, I still can’t believe I’m here. My application was pretty last-minute, completed when I was in a state of droopiness and scholarship-application-hyperdrive. But I got on a plane from the Midwest, went from cloudy, 20 degrees with windchill making it feel like 0 to sunny, 77 degrees with mild winds making it feel still 77 degrees.
If you see a bug in the code, it's probably dying
A guest post by turtlekiosk on 13 Jan 2015
Winter Break Of Code Day 1
I woke up this morning feeling like this routine was normal, instead of implausible. Two days ago, I was in New York City, riding the train with millions of other commuters in the freezing snow. Today, I went surfing on a beach in beautiful Kauai. In the same absurd fashion, I shared meals, stories, and workspaces with people, who days earlier, I had only read about and admired from afar. The promises of the Winter Break of Code seem impossible: a vacation in paradise, large milestones of work to be met, a welcoming space with talented companions. But when Moxie came into the bedroom this morning strumming his ukulele to wake us for the daily morning stand-up, up we were, ready to claim the small victories in the browser extension project, the Signal iOS client, and the Android applications from the day prior and to lay out plans to further the state of user-friendly secure communication tools.
Winter Of Code Lineup 2014-2015
moxie0 on 16 Dec 2014
Every year when we do this kind of call for proposals, our experience from past events sets our expectations higher. Even with really high expectations this time around, we were blown away by the number of high-quality proposals we received for this winter. It’s inspiring to know how many people are thinking seriously about the development of privacy-enhancing technology, and we hope that one day we’ll have a space large enough to accept all the proposals that we wish we could.
The lineup for this January is set to be really great:
At Open Whisper Systems, our goal is to make private communication simple. For the past three years, we’ve been developing a modern, open source, strong encryption protocol for asynchronous messaging systems, designed to make seamless end-to-end encrypted messaging possible.
Today we’re excited to publicly announce a partnership with WhatsApp, the most popular messaging app in the world, to incorporate the TextSecure protocol into their clients and provide end-to-end encryption for their users by default.
Winter Of Code
moxie0 on 20 Oct 2014
This January, Open Whisper Systems will be hosting a Winter Break Of Code. We’ve managed to get access to a large beachfront house in Kauai for three weeks, and we’re inviting people to join us. If you’re interested in spending one to three weeks in Hawaii working collaboratively on an Open Source project to make private communication simple, we’ll take care of your airfare and housing so that you can be there.
Winter Break Of Code is an opportunity for designers, developers, writers, strategists, and creative thinkers interested in privacy and security to spend some time contributing to privacy-related projects in a retreat-like setting with other co-conspirators. Think of it as an extended hackathon, but with your travel expenses paid, and with breaks for surfing, hiking, swimming, and just generally being in Kauai.
Everything that Open Whisper Systems produces is free and Open Source. We’ve been working on apps like Signal, TextSecure, RedPhone, and Flock for years now, because we believe that it’s possible to develop well-designed apps that are both privacy-preserving and a joy to use.
Free, Worldwide, Encrypted Phone Calls for iPhone
moxie0 on 29 Jul 2014
At Open Whisper Systems, we want everyone to have access to advanced secure communication tools that are as easy and reliable to use as making a normal phone call or sending a normal text message.
Over the past year, we’ve been working to bring the privacy software we’ve developed for Android to the iPhone, and today we’re releasing Signal – free, worldwide, encrypted voice calls for iPhone, and fully compatible with RedPhone for Android.
Flock, Private Contact and Calendar Cloud Sync.
rhodey on 21 Jul 2014
At Open Whisper Systems, we believe users should have both privacy and powerful services. Today we’re releasing Flock, a private cloud sync service for your personal data.
Your contacts and calendars belong to you. So does your privacy. Flock makes it possible to have both.
Private Group Messaging
moxie0 on 05 May 2014
One of the major features we introduced in the TextSecure v2 release was private group chat. We believe that group chat is an important feature for encrypted communications projects, so we wanted to try to summarize some of the existing work in this area, as well as how TextSecure’s group chat protocol functions.
The New TextSecure: Privacy Beyond SMS
moxie0 on 24 Feb 2014
Today’s release of TextSecure is the final step in the transition from a private SMS app to a private asynchronous IM app that does not depend on SMS/MMS.
Using the lessons we’ve learned from the SMS environment over the past four years, we’ve developed an open protocol for asynchronous chat that enables private communication instantly with friends, private groups for real-time collaboration, and the ability to quickly and seamlessly share media privately – all without depending on SMS.
Android Contacts, the Social Graph Collider
rhodey on 13 Jan 2014
Winter Break of Code, Day Seven

Spring Break of Code 2013 I cut open my foot and hand while surfing; both wounds easily warranted stitches. Winter Break of Code 2014 I banged the top of my foot surfing over some coral; the cuts were sealed within minutes. Spring Break of Code 2013 I struggled with the Android SDK, while Winter Break of Code 2014 I caught myself taking a few too many short-cuts. On day zero nothing is easy, but over time you improve, spilling a little less blood every time.
Moments to keep
meskio on 12 Jan 2014
Winter Break of Code, Day Six
A lot of great memories will stay with me after this intense week. The house surrounded by palm trees, people with computers in every corner, laying down on a sofa, chatting on the balcony, and sitting down on the carpet. The surf and hiking breaks on this astonishing Kauai’s landscape, sharp mountains covered by forests falling into beaches of fine sand and fun waves. The nights spiced with Moxie’s tasty cocktails and long deep conversations about the meaning of life, the internet and everything.

The value of our confidences
abolishme on 11 Jan 2014
Winter Break of Code, Day Five

Understanding digital privacy under capitalism
If commodities could speak, they would say this: our use-value may interest men [sic], but it does not belong to us as objects. What does belong to us as objects, however, is our value. Our own intercourse as commodities proves it. We relate to each other merely as exchange-values.
– Marx, Capital: A Critique of Political Economy, Vol 1.
Thus spake the commodity
Marx saw modernity more acutely than most of his contemporaries, and provided a description of capitalism that remains, in my opinion, quite useful.
However, we must be brave enough to attempt to understand his description of the relationship between commodity and value in the context of a world very different from Industrial Revolution-era Europe. That is, one which includes the strange new primordial soup of the internet and capital.
Imagine, as Marx expects of us in the passage above, that an “internet” commodity could speak. What would it say?
Winter Break of Code, Day Four
At the Open Whisper Systems spring break of code in 2013, I started work on TextSecure iOS. People are chomping at the bit to use our software on iOS. After a hiatus from the project, I’ve been happy to return to it over the last few months, joining some other contributors, including Frederic Jacobs as co-lead, Alban Diquet, and Claudiu-Vlad Ursache submitting pull requests, even over the holidays, with important cryptographic storage and UI-polishing contributions, and Bitcoin donations coming in from around the world.
Contribute code or coins.
Design of Crypto
A guest post by mkhandekar on 09 Jan 2014
Winter Break of Code, Day Three
We are at the halfway point of Winter Break of Code. We have two homes near the beach shared by 12 people. 10 of us are working on the apps & website and 2 are leading up delicious dinner efforts. We’ve spent time on the beach, in the ocean, in the mountains, and of course working. Concepts for future startups and tactics about self-publishing books are brewing, and conversations are lined with politics and activism. Work sessions are focused on making cryptography usable in existing Android apps and soon-to-be-released iPhone apps.

Better than cake
A guest post by liliakai on 08 Jan 2014
Winter Break of Code, Day Two
By all rights, I should not be here. My application was last-minute to say the least, and little more than a casual note that I’d be down to reprise my role from SBoC as web hacker for whispersystems.org. Maybe it was because of my work in the previous months on tweaking the site layout to be responsive, or because @bcrypt (who is infinitely more qualified) was too dedicated to her work at the EFF to take the time off, or because my birthday happened to fall on this week, but for one reason or another, the universe smiled, and here I am.

Roosters and a mountain of design
A guest post by mcginty on 07 Jan 2014
Winter Break of Code, Day One

The Winter Break of Code, being closely linked by name to the season of Winter, began with a calm trickle of ex{hausted,cited} people carrying laptops and cell phone collections after a parade of delays and weather issues. Off the plane after a pitch-black descent, the humid fresh smell distinct to this place along with my feet landing on soil was a good hint that we were indeed on an island and this was actually happening. It was very welcome.
The Difficulty Of Private Contact Discovery
moxie0 on 03 Jan 2014
Building a social network is not easy. Social networks have value proportional to their size, so participants aren’t motivated to join new social networks which aren’t already large. It’s a paradox where if people haven’t already joined, people aren’t motivated to join.
The trouble is that while building a social network is hard, most interesting software today is acutely “social.” Even privacy-enhancing technology, which seems anathema to the aesthetic of social networking, is tremendously social. For people to effectively use private communication software like TextSecure, they need to be able to know how to contact their friends using TextSecure.
At Open Whisper Systems, we often get emails from people who’d like to donate money to the project. For an OSS project, particularly one that aspires to a collective sense of ownership, handling donations is not always entirely straightforward.
The fundamental contradiction is that while donations are meant for a project, they’re traditionally sent to a person. Even if a project sets up a bank account, there are still only a few people who have access to the money itself, and distributing it appropriately can be hard to figure out.
It’s never been clear to us how we should handle small donations, so oftentimes when people ask about donating, we just tell them that the best way to help is to use the software, spread the word, and file well-documented bugs when they find them. Which is true! But it’d also be great if we had a nice system for handling donations that matched our objectives for collective ownership.
WBoC Lineup
moxie0 on 11 Dec 2013
After our wonderful experience with Spring Break Of Code, we were excited to try this again. Even with high expectations based on our experience in the Spring, the response was still better than what we could have hoped for. The hundreds of high-quality proposals we received were really inspiring, and we hope that one day we can get a space large enough for all of the amazing people who are passionate about the development of privacy-enhancing technology.
We think the final lineup of those attending in January is going to be great:
TextSecure, Now With 10 Million More Users
moxie0 on 09 Dec 2013
At Open Whisper Systems, we’re working to both advance the state of the art for secure communication and also reduce the friction required for ordinary people to make use of it. We want everyone to have access to advanced secure communication methods that are as easy and reliable to use as making a normal phone call or sending a normal text message.
With these goals in mind, we’ve been working with CyanogenMod over the past few months. CyanogenMod is an open source aftermarket Android firmware distribution with ten million users and ~20k installs a day. Their rapid growth is beginning to rival Microsoft for the third-largest smartphone OS distribution.
As of today, the TextSecure protocol will begin shipping as part of the CyanogenMod OS-level SMS provider, in an effort to provide completely transparent end-to-end text message encryption between all of their users.
Advanced cryptographic ratcheting
moxie0 on 26 Nov 2013
At Open Whisper Systems, we’ve been working on improving our encrypted asynchronous chat protocol for TextSecure. The TextSecure protocol was originally a derivative of OTR, with minor changes to accommodate it for transports with constraints like SMS or Push. Some of the recent changes we’ve made include simplifying and improving OTR’s deniability, as well as creating a key exchange mechanism for asynchronous transports. Our most recent change incorporates what we believe to be substantial improvements to OTR’s forward secrecy “ratchet.”
Winter Break Of Code
moxie0 on 23 Oct 2013
At Open Whisper Systems, we’re focused on creating easy-to-use privacy-enhancing technology. Our projects are free, Open Source, and tend to be oriented around the mobile environment. We’ve been working on apps like TextSecure and RedPhone (which provide secure text messages and secure phone calls) for years now, because we believe that it’s possible to develop well-designed secure communication tools that are both privacy-preserving and a joy to use.
This winter, we’d like to invite you to join us for “Winter Break Of Code,” a week-long free trip to Kauai for anyone who’d like to spend a week working on this type of easy-to-use privacy-enhancing technology in a collaborative environment. We’ve rented a large beachfront house on the north coast of Kauai for everyone to stay in, and we’ll pay for your airfare. While there, you can split your time between island living and working on an Open Whisper Systems-related privacy project that you propose.
Alpine Hackathon Reportback
A guest post by meskio on 22 Oct 2013
My cell phone used to be a black and white Nokia until a couple of weeks ago when I decided to enter in the smartphone world. Now that there are more mobile devices connected to the internet than computers, I think it’s time for me as well to discover the possibilities of this technology. During this few weeks I’ve been playing with my new toy, checking how to secure it, and seeing what free software is around to use cryptography on it.
Open Whisper Systems Alpine Hackathon
A guest post by corbett on 27 Sep 2013
From October 11th to October 13th, we’ll be hosting an informal Open Whisper Systems Alpine Hackathon for those in or around Zurich, Switzerland who would like to contribute to Open Whisper Systems-related projects in a collaborative setting with other co-conspirators.
Forward Secrecy for Asynchronous Messages
moxie0 on 22 Aug 2013
Traditionally, asynchronous messaging systems such as email have relied on protocols like PGP or S/MIME for cryptographic security. These protocols work the way most people are familiar with: one who wishes to receive encrypted email advertises a public key, and those wishing to send encrypted email to that person encrypt their outgoing message with that public key.
Simplifying OTR deniability.
moxie0 on 27 Jul 2013
At Open Whisper Systems we help develop TextSecure, an encrypted chat application for Android. TextSecure was designed as a general purpose SMS/MMS client which would also automatically encrypt conversations when communicating with other TextSecure users. For those encrypted sessions, TextSecure uses a compact derivative of the well-known OTR protocol.
We’re currently in the process of transitioning TextSecure to use a device’s data channel as a transport for communication with other TextSecure users whenever possible. This enables communication with the upcoming TextSecure for iOS, helps users avoid SMS fees, and obscures conversation metadata from telcos.
The transition to a new transport is also a good opportunity for us to evaluate and introduce additional cryptographic protocol changes. Below is one cryptographic protocol change we’re thinking of making that we’d welcome feedback on.
Open Whisper Systems is coming to iPhone!
moxie0 on 25 Jul 2013
Open Whisper Systems is a project focused on developing Open Source security and privacy apps for the mobile environment. With all of the recent discussion about PRISM, Boundless Informant, and FISA orders, there has been a surge of new users and inquiries about how to get involved.
SBoC Farewell
moxie0 on 31 Mar 2013
The last code committed, the final waves surfed in to the shore, the closing sunset of Spring Break Of Code.

Call Quality Metrics
emblem on 30 Mar 2013
Spring Break Of Code, Day Six
Because secure systems aren’t valuable if they’re not used, Whisper Systems has always focused on delivering strong cryptography alongside a great user experience. That’s the reason call quality has always been a priority in RedPhone’s development.
We know that, for many users, RedPhone has consistently delivered a call quality experience comparable to commercial mobile VoIP solutions. But we also hear from users who report problems like dropped calls, distracting levels of echo and latency, or inaudibly low in-call volume. While we investigate these reports and attempt to resolve them, we don’t have a clear view of what situations cause RedPhone’s call quality to degrade, or how to prioritize our development efforts.
All The Things That Pull And Push
A guest post by abolishme on 29 Mar 2013
Spring Break Of Code, Day Five

I know very well that each and every crisis of modernity is concentrating, concatenating, and seating more deeply into everyday life. I know the struggles of the world’s unseen and unheard are being subsumed – appropriated – under and into the framework of a liberal democracy, leaving those at the periphery still under the yoke of capital. The Right further entrenches itself into political discourse, both in the United States, and (more extremely) abroad (Finland, Greece, … et al.). The Left is no less problematic: reiterating the petty values of social democracy, negotiating the terms of our entrapment within capitalism. Every season, new horrors fall from the clouds and rise from the seas as industrial civilization demonstrates that terraforming can also work in reverse. The world’s genetic library – the most prime commons, if ever one existed – is rapidly contracting via extinction, privatization, and engineering. The colossal failure of ideology in the twentieth century has left the radicals of today no other choice but to see themselves as “post-ideological”. This is a deeply concerning conundrum, as ideology survives in post-ideology, different only to the extent that it is less apparent. Yes, it seems like we are living in end times – an entire era of Apocalypse – made only more insidious by our optimism in its shadow.
Spring Break Of Code, Day Four
The main sound on top of the ocean is the click clack of laptop keys, and the jangle of test calls and SMSes. A neighbor stopped by to comment that we must be the next Facebook, the next Google; working instead of surfing made sense in his mind only in the land of money at the end of the tunnel. He loaned us his stand up paddle boards, surely expecting a return on investment 10 fold down the line when we exited into the sunset. A journalist visiting Open Whisper Systems’ Spring Break of Code commented that she expected more philosophy, politics, and conversation. After all this group is composed of people who are not only technologists, but also open source evangelists, activists, and humanists. Lilia went over some of the why, but practically anyone could see we were concentrating on the how, and in the frenzied silence it was clear that a common philosophy was assumed and what bound us here was the challenges in the technology to power that philosophy.
Streamlining TextSecure Settings
A guest post by liliakai on 27 Mar 2013
Spring Break Of Code, Day Three
I am no stranger to Hawaii. Although I’ve never lived here myself, I’ve visited the islands perhaps a dozen times. My grandmother and my father were born and raised here. My mother attended college here. I have aunts, uncles, and cousins who’ve lived on various islands, moved away, came back, moved away and back again. I even have Native Hawaiian blood in my veins.
But this trip is different. This time it’s not about family or heritage. This time, I have a mission: to make secure text messaging and calling easier, more accessible, and more prevalent.
Highly Unconventional Suggested First Aid
A guest post by rhodey on 26 Mar 2013
Spring Break Of Code, Day Two
“I am torn on how best to introduce myself out of context like this, the idea of rattling off facts from my resume is my first instinct, but that seems terribly conventional. With the goal of introducing myself and the entirety of my character, my second (highly unconventional) instinct is to link you to my online dating profile with the prayer that such an action would be taken in the desired context. Through my indecision I hope to explain who I am and why I would like to travel across the country to be involved with the Institute for Disruptive Studies. So here goes…”
Dirigibles, Chinese Junk Rigs, and Surfboards
A guest post by isislovecruft on 25 Mar 2013
Spring Break Of Code, Day One.
One of the first times I met up with Moxie while travelling, we met at a dive bar in San Francisco’s Mission District, packed with hipsters. I had nineteen years, a modified state ID card, and just hitchhiked into town. We sat at the bar, and both ordered well gin and tonics.
I had a proposal, the sort of get-rich-quick scheme it seems that only 18th century pirates and lazy hacker-squatters are capable of contriving: We fly to China. Then, we spend a few grand purchasing a Chinese junk rig, and equip it with a system of pulleys so that we can man the sails from the cockpit, solo if necessary. Next, we fill the cabin with about as much potable water as we can carry and enough dried food to stave off starvation, and set a course across the northern arc of the Pacific – avoiding the treachery of the South Seas – for San Francisco. The choice of vessel was key, the battened sails and flattened hull of a Chinese junk rig make it arguably one of the safest ships to make a transoceanic voyage alone, not to mention the financial incentives: being rare in the Americas, a well-kept junk rig would go for anywhere from $50,000 to $250,000 USD – not to mention grant you free slip fees at just about any marina from Anchorage to Punta Arenas. How could anyone turn down such a preposterous plot which included adventure on the high seas, a high mortality risk, riches and notoriety?
Merchandise
moxie0 on 06 Mar 2013
It’s a busy time here at the Open Whisper Systems factory, and we need all the floor space we can get. We still have some first-edition T-Shirts that are taking up some space, so we’re offering them to you for the cost of shipping and handling.
There are two designs available in a number of sizes:
SBoC Lineup
moxie0 on 01 Mar 2013
We were excited about our Spring Break Of Code announcement, but the response was better than we anticipated: over 100 extremely impressive proposals from folks around the world who are passionate about pushing the envelope of security and privacy software. After reading all the proposals, we really wish we’d rented a bigger house.
We think the final lineup of accepted proposals is great:
Client-side call quality
emblem on 18 Feb 2013
In our previous post, we discussed the global infrastructure that allows RedPhone clients to find low-latency servers when establishing a call. This post discusses the techniques we use to retain call quality when network conditions are less than ideal.
Creating a low-latency calling network
moxie0 on 31 Jan 2013
RedPhone is our mobile app for end-to-end encrypted voice calls. When we talk about RedPhone, we tend to emphasize the cryptography, and how using it can help keep your communications safe. What we don’t talk about as much is the VoIP application underneath all of that, which it turns out was actually the hard part.
When we were developing RedPhone, we discovered that the cryptographic aspects of it were relatively straightforward. What we didn’t anticipate was how difficult the mechanics of delivering high-quality, low-latency, and highly available voice communication would be.
This describes the basic strategy we developed for the network side of low-latency and highly available calls.
Spring Break Of Code
moxie0 on 23 Jan 2013
This Spring will be the first Open Whisper Systems Spring Break Of Code, a week-long, expenses-paid retreat to Maui for folks who like software development, security, and the beach. We’ve rented a large beachfront house on the west coast of Maui for everyone to stay in, and will pay for your airfare. While there, you can split your time between island living and working on an Open Whisper Systems-related project that you propose.

A New Home
moxie0 on 21 Jan 2013
Whisper Systems was a company focused on the development of mobile security software, which was acquired by Twitter in late 2011. Twitter very generously made some of the Whisper Systems software available under an Open Source license (GPLv3), which has since been under open development by the community. The software has seen a number of new releases based on that open development, and we’ve been calling the project for this continued work “Open Whisper Systems.” Welcome to the project’s new home.





